

Data confidentiality is crucial for your business. A breach can lead to severe consequences, including financial losses and reputational damage. In 2023, the average cost of a data breach reached 4.45 million U.S. dollars. Small businesses face costs ranging from $36,000 to $50,000. Nearly 29% of businesses lose revenue after a breach. You must take proactive steps to protect sensitive information. Tools like FineDataLink, FineReport, and FineBI can help safeguard your data, ensuring it remains confidential and secure.
Identifying and Classifying Data Confidentiality
Understanding the types of data your business handles is crucial for maintaining confidentiality. Different data types require varying levels of protection. Let's explore these categories and how you can classify them effectively.
Understanding Different Types of Data
Personal Identifiable Information (PII)
Personal Identifiable Information (PII) includes details that can identify an individual. This data encompasses names, addresses, social security numbers, and more. Protecting PII is vital because breaches can lead to identity theft and legal consequences. Regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) mandate strict handling of PII to safeguard consumer rights.
Financial Data
Financial data involves sensitive information related to transactions, bank accounts, and credit card details. Unauthorized access to this data can result in significant financial losses. The Gramm-Leach-Bliley Act (GLBA) requires companies offering financial products to explain their information-sharing practices and safeguard sensitive data. Violations can lead to hefty fines, emphasizing the importance of securing financial data.
Intellectual Property
Intellectual property includes proprietary information such as patents, trademarks, and trade secrets. Protecting this data is essential to maintain a competitive edge. Unauthorized access or leaks can result in financial losses and damage to your business reputation. Implementing robust security measures ensures that your intellectual property remains confidential.
Data Classification Techniques
Sensitivity Levels
Classifying data based on sensitivity levels helps prioritize protection efforts. You can categorize data as public, internal, confidential, or restricted. Public data requires minimal protection, while restricted data demands the highest security measures. By understanding the sensitivity of your data, you can allocate resources effectively to safeguard it.
Data Inventory and Mapping
Creating a data inventory and mapping it across your organization is crucial for effective data management. This process involves identifying where data resides, how it flows, and who has access to it. By maintaining a comprehensive data map, you can ensure compliance with regulations like GDPR and CCPA. Regular audits of your data inventory help uncover hidden liabilities and ensure transparency with customers about how their data is utilized.
"Companies should know the where, why, and how of data collection. They must understand their obligations for stewardship across the data life cycle, from creation through destruction."
By understanding and classifying your data, you can implement targeted measures to protect it. This proactive approach not only ensures compliance with legal requirements but also builds trust with your customers by demonstrating your commitment to data confidentiality.
Implementing Access Controls and Encryption to Ensure Data Confidentiality
To protect your business's sensitive data, you must implement robust access controls and encryption methods. These measures ensure that only authorized personnel can access confidential information, safeguarding it from unauthorized access and potential breaches.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a crucial strategy for managing who can access specific data within your organization. By defining user roles and assigning permissions, you can control access effectively.
Defining User Roles
Begin by identifying the various roles within your organization. Each role should have specific responsibilities and access needs. For instance, a financial analyst might need access to financial data, while a marketing manager requires access to customer insights. Clearly defining these roles helps you tailor access permissions to meet each role's requirements.
Assigning Permissions
Once you've defined user roles, assign permissions based on the principle of least privilege. This means granting users the minimum level of access necessary to perform their job functions. By doing so, you minimize the risk of unauthorized access to sensitive data. Access Control Software can assist in managing these permissions, ensuring that employees only access the data relevant to their roles.
Encryption Methods
Encryption is a powerful tool for protecting data confidentiality. It involves converting data into a coded format that can only be deciphered with the correct key. Implementing strong encryption methods ensures that even if data is intercepted, it remains unreadable to unauthorized parties.
Data-at-Rest Encryption
Data-at-rest encryption protects data stored on devices or servers. This includes files, databases, and backups. By encrypting data at rest, you ensure that it remains secure even if physical devices are lost or stolen. Enterprise Server Encryption Software offers centralized management of encryption across various platforms, including PC, Mac, and Linux, providing a comprehensive solution for data-at-rest protection.
Data-in-Transit Encryption
Data-in-transit encryption secures data as it travels across networks. This is crucial for protecting information sent via email, transferred between servers, or accessed through cloud services. Using strong encryption protocols, such as TLS (Transport Layer Security), ensures that data remains confidential during transmission. Data Encryption Software provides robust security with 128-bit or 256-bit AES encryption, safeguarding files stored on cloud services like Google Drive and Dropbox.
By implementing RBAC and encryption methods, you create a secure environment for your business's data. These measures not only protect against unauthorized access but also demonstrate your commitment to data confidentiality, building trust with your customers and stakeholders.
Developing Data Confidentiality Policies
Creating robust data confidentiality policies is essential for safeguarding sensitive information in your business. These policies provide a structured approach to managing data and ensuring compliance with legal requirements.
Policy Framework
Establishing Clear Guidelines
You must establish clear guidelines to protect data confidentiality. Start by defining the types of data your business handles and the specific measures required to protect each type. Outline procedures for data collection, storage, and sharing. Ensure that all employees understand their responsibilities regarding data protection. Clear guidelines help maintain consistency and prevent unauthorized access to sensitive information.
Regular Policy Reviews
Regularly reviewing your data confidentiality policies is crucial. As technology and regulations evolve, your policies must adapt to remain effective. Schedule periodic reviews to assess the relevance and effectiveness of your guidelines. Involve key stakeholders in the review process to gather diverse perspectives and insights. By keeping your policies up-to-date, you ensure that your business remains compliant and prepared for potential threats.
Incident Response Plan
Identifying Breach Scenarios
Identifying potential breach scenarios is a vital step in developing an incident response plan. Consider various situations that could compromise data confidentiality, such as cyberattacks, employee negligence, or physical theft. By anticipating these scenarios, you can develop targeted strategies to address them. Understanding the risks your business faces allows you to allocate resources effectively and prioritize response efforts.
Response and Mitigation Strategies
Developing response and mitigation strategies is essential for minimizing the impact of data breaches. Outline clear steps for containing breaches, recovering data, and communicating with affected parties. Ensure that your plan includes legal obligations, such as notifying authorities and impacted individuals. Regularly train your staff on these protocols to improve overall incident response effectiveness. Well-prepared employees can significantly reduce potential damages and help your business recover swiftly from security incidents.
"An effective incident response plan outlines steps to take in case of a data breach, including communication protocols, containment strategies, data recovery procedures, and legal obligations."
By establishing a comprehensive policy framework and incident response plan, you create a strong foundation for data confidentiality in your business. These measures not only protect sensitive information but also demonstrate your commitment to data security, building trust with your customers and stakeholders.
Ensuring Data Confidentiality with Relevant Regulations
Understanding and complying with data protection regulations is crucial for maintaining data confidentiality in your business. These regulations set the standards for how you should handle personal data, ensuring that you respect consumer rights and maintain robust security practices.
Understanding Regulatory Requirements
GDPR
The General Data Protection Regulation (GDPR) is a comprehensive data protection law in the European Union. It mandates that you must have a legitimate reason for collecting personal data and requires you to protect this data from unauthorized access. GDPR emphasizes transparency, giving individuals the right to know how their data is being used. You must also ensure that data is collected for specified, explicit, and legitimate purposes. Non-compliance can result in hefty fines, making it essential for you to align your data practices with GDPR standards.
CCPA
The California Consumer Privacy Act (CCPA) is often referred to as a 'GDPR lite' version. It provides California residents with rights over their personal data, including the right to know what data is collected and the right to request deletion. CCPA requires you to disclose your data collection practices and allows consumers to opt-out of the sale of their personal information. While it shares similarities with GDPR, CCPA focuses more on consumer rights within California. Compliance with CCPA helps you avoid penalties and demonstrates your commitment to data privacy.
Implementing Compliance Measures
Regular Audits
Conducting regular audits is essential for ensuring compliance with data protection regulations. Audits help you assess your data privacy practices, including how you store, collect, process, and use customer data. By regularly reviewing these practices, you can identify potential vulnerabilities and address them promptly. Audits also ensure that your business remains aligned with GDPR, CCPA, and other relevant regulations. This proactive approach not only helps you avoid penalties but also builds trust with your customers by demonstrating your dedication to data security.
Documentation and Reporting
Maintaining thorough documentation and reporting is a key aspect of compliance. You should document your data processing activities, including the types of data collected, the purposes for collection, and the security measures in place. This documentation serves as evidence of your compliance efforts and can be crucial in the event of an audit or investigation. Regularly updating your documentation ensures that it reflects any changes in your data practices or regulatory requirements. By keeping detailed records, you can demonstrate your awareness of cybersecurity concerns and your commitment to protecting consumer data.
"Organizations must respect consumer rights, have legitimate reasons for data collection, and maintain security practices."
By understanding regulatory requirements and implementing compliance measures, you can ensure data confidentiality in your business. These steps not only protect sensitive information but also reinforce your commitment to data privacy, enhancing your reputation and building trust with your customers.
Educating Employees on Data Confidentiality Practices
Educating your employees about data confidentiality is crucial. They are the first line of defense against data breaches. By equipping them with the right knowledge and skills, you can significantly reduce the risk of unauthorized access to sensitive information.
Training Programs
Training programs play a vital role in enhancing your employees' understanding of data confidentiality. They provide the necessary tools and knowledge to handle data securely.
Regular Workshops
Regular workshops offer hands-on experience. They allow employees to engage with real-world scenarios and learn how to respond effectively. You should schedule these workshops frequently to keep your team updated on the latest security practices. Interactive sessions encourage participation and help reinforce learning.
Online Courses
Online courses provide flexibility. They allow employees to learn at their own pace and revisit materials as needed. You can offer a variety of courses covering different aspects of data security. This approach ensures that all employees, regardless of their role, have access to relevant information. Online platforms often include quizzes and assessments to test understanding and retention.
"Cybersecurity involves more than having the best hardware and software — it also involves employees. Educating all employees is a fundamental best practice."
Creating a Security-Conscious Culture
Creating a security-conscious culture within your organization is essential. It fosters an environment where data confidentiality is a shared responsibility.
Encouraging Reporting of Security Incidents
Encourage your employees to report security incidents promptly. Establish clear channels for reporting and ensure that employees feel comfortable using them. Quick reporting can prevent minor issues from escalating into major breaches. Recognize and reward employees who take the initiative to report potential threats.
Rewarding Good Security Practices
Rewarding good security practices motivates employees to remain vigilant. Implement a recognition program that highlights individuals or teams who demonstrate exemplary data protection behaviors. Rewards can range from public acknowledgment to tangible incentives. This approach not only boosts morale but also reinforces the importance of maintaining data confidentiality.
"Organizations must implement appropriate technical and organizational measures to protect data from breaches or other security incidents. This involves encryption, access controls, regular security audits, and employee training to maintain confidentiality."
By investing in training programs and fostering a security-conscious culture, you empower your employees to protect your business's data. These efforts not only enhance data confidentiality but also build a resilient organization capable of withstanding potential security threats.
Regularly Updating and Auditing Data Confidentiality Measures
To maintain data confidentiality, you must regularly update and audit your security measures. These actions ensure that your systems remain robust against evolving threats and vulnerabilities.
Security Software Updates
Keeping your security software up-to-date is crucial. Updates often include patches for known vulnerabilities, enhancing your system's defenses.
Patch Management
Patch management involves identifying, acquiring, and applying software updates. You should prioritize critical patches that address severe vulnerabilities. By doing so, you minimize the risk of exploitation by cybercriminals. Implementing an automated patch management system can streamline this process, ensuring timely updates across all devices.
Vulnerability Assessments
Conduct regular vulnerability assessments to identify potential weaknesses in your system. These assessments help you understand where your defenses may fall short. Use specialized tools to scan your network and applications for vulnerabilities. Address any issues promptly to prevent unauthorized access to sensitive data.
"Regular vulnerability assessments are essential for identifying and addressing potential security gaps before they can be exploited."
Conducting Security Audits
Security audits provide a comprehensive review of your data protection measures. They help ensure compliance with regulations and identify areas for improvement.
Internal Audits
Internal audits involve your organization's team assessing internal controls, policies, and procedures. These audits allow you to evaluate your current security practices and make necessary adjustments. For small and medium-sized enterprises (SMEs), internal audits can be more time-efficient, as managers are already familiar with the organization's processes.
Third-Party Audits
Third-party audits offer an unbiased assessment of your security practices. External experts conduct these audits, providing valuable insights into your data protection measures. Large organizations, with substantial infrastructure and sensitive data, often benefit from third-party audits. These audits ensure that your security measures meet industry standards and regulatory requirements.
"External audits provide an unbiased assessment of your organization's security practices, ensuring compliance and identifying areas for improvement."
By regularly updating your security software and conducting thorough audits, you strengthen your data confidentiality measures. These proactive steps not only protect sensitive information but also demonstrate your commitment to maintaining a secure environment for your business and its stakeholders.
Leveraging FanRuan's Solutions for Data Confidentiality
In today's digital age, ensuring data confidentiality is paramount for any business. FanRuan offers a suite of solutions designed to protect your sensitive information. These tools not only enhance security but also streamline data management processes.
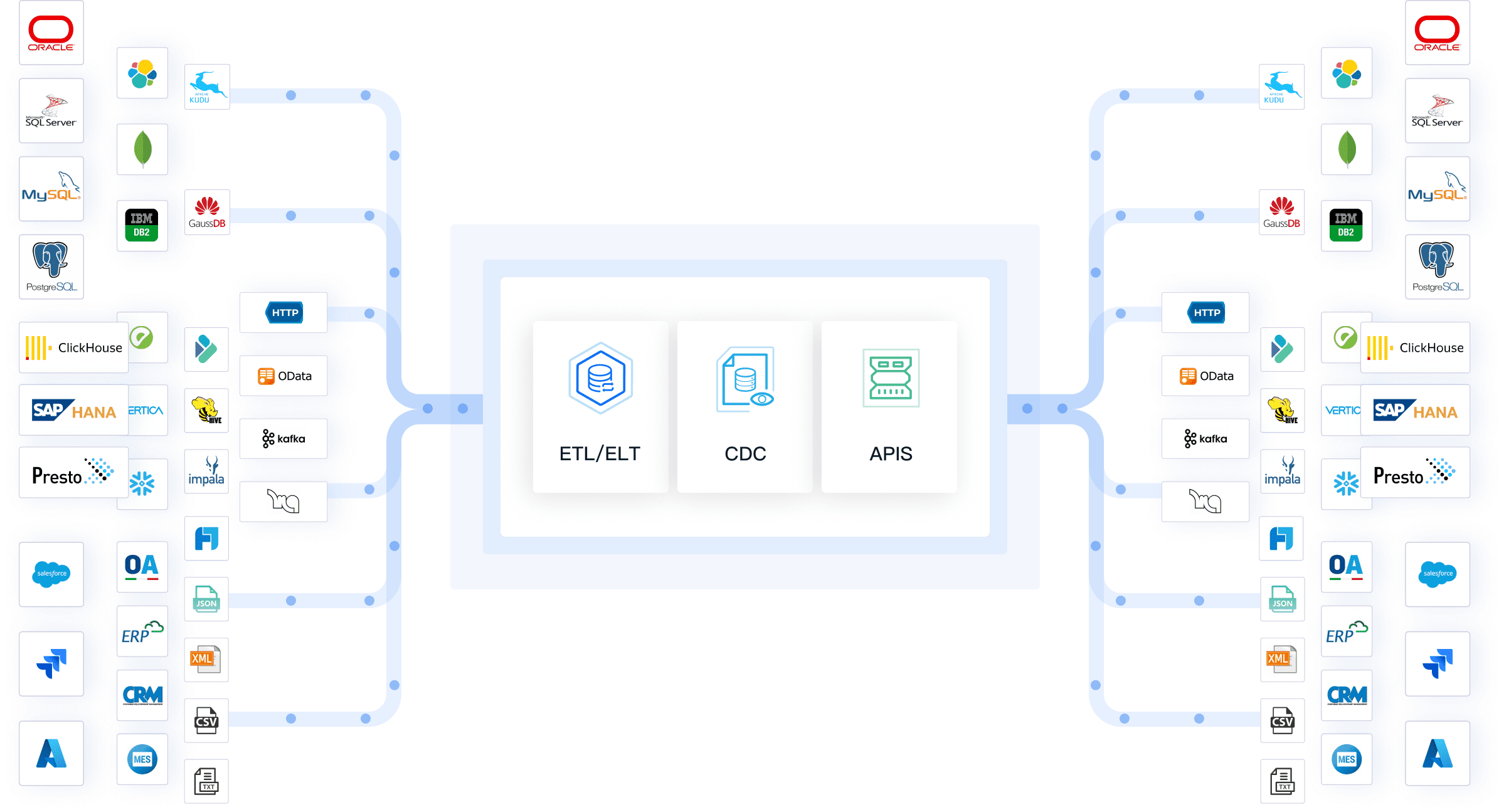
FineDataLink for Secure Data Integration
FineDataLink serves as a comprehensive platform for secure data integration. It simplifies complex data tasks with its low-code approach, making it accessible even to those with limited technical expertise. By using FineDataLink, you can synchronize data in real-time across various systems, ensuring that your information remains consistent and up-to-date. This platform supports over 100 common data sources, allowing seamless integration and synchronization. With its robust security measures, including role-based access control and multi-factor authentication, FineDataLink ensures that only authorized personnel can access sensitive data.
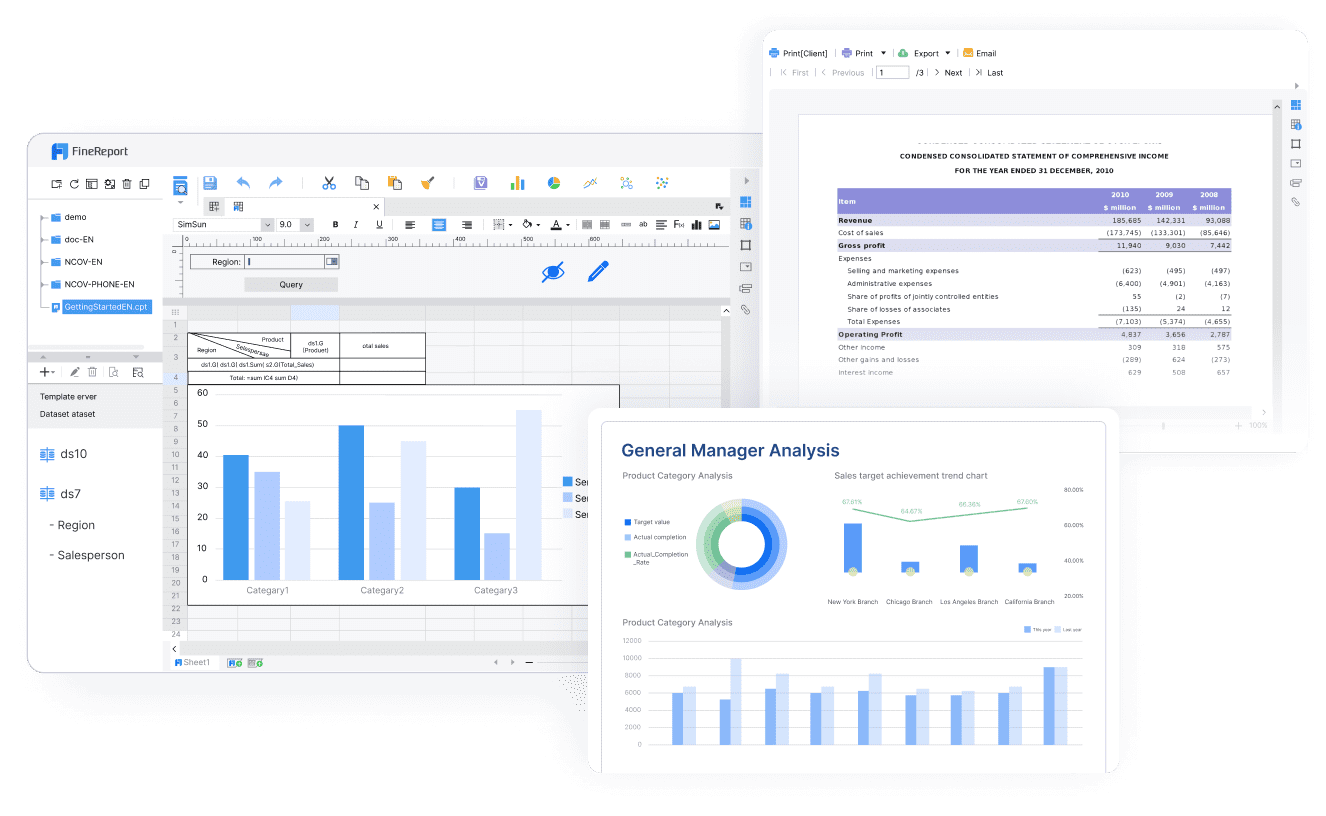
FineReport for Confidential Reporting
When it comes to reporting, FineReport stands out as a powerful tool for creating confidential reports. It allows you to generate pixel-perfect documents and dashboards, ensuring that your data is presented accurately and professionally. FineReport connects to various data sources, enabling you to uncover deeper insights and make informed decisions. Its flexible report designer and diverse visualization options make it easy to tailor reports to your specific needs. By using FineReport, you can maintain data confidentiality while delivering comprehensive reports to stakeholders.
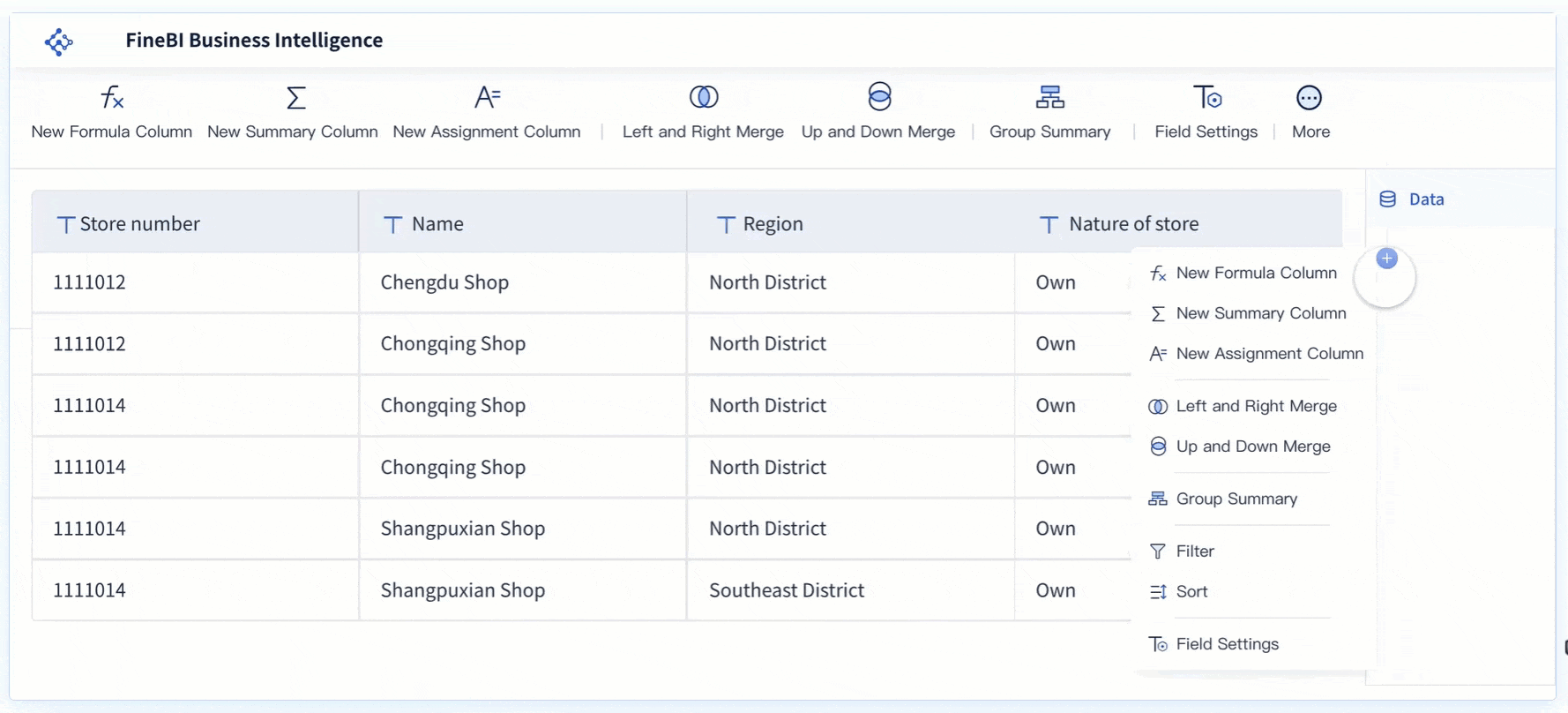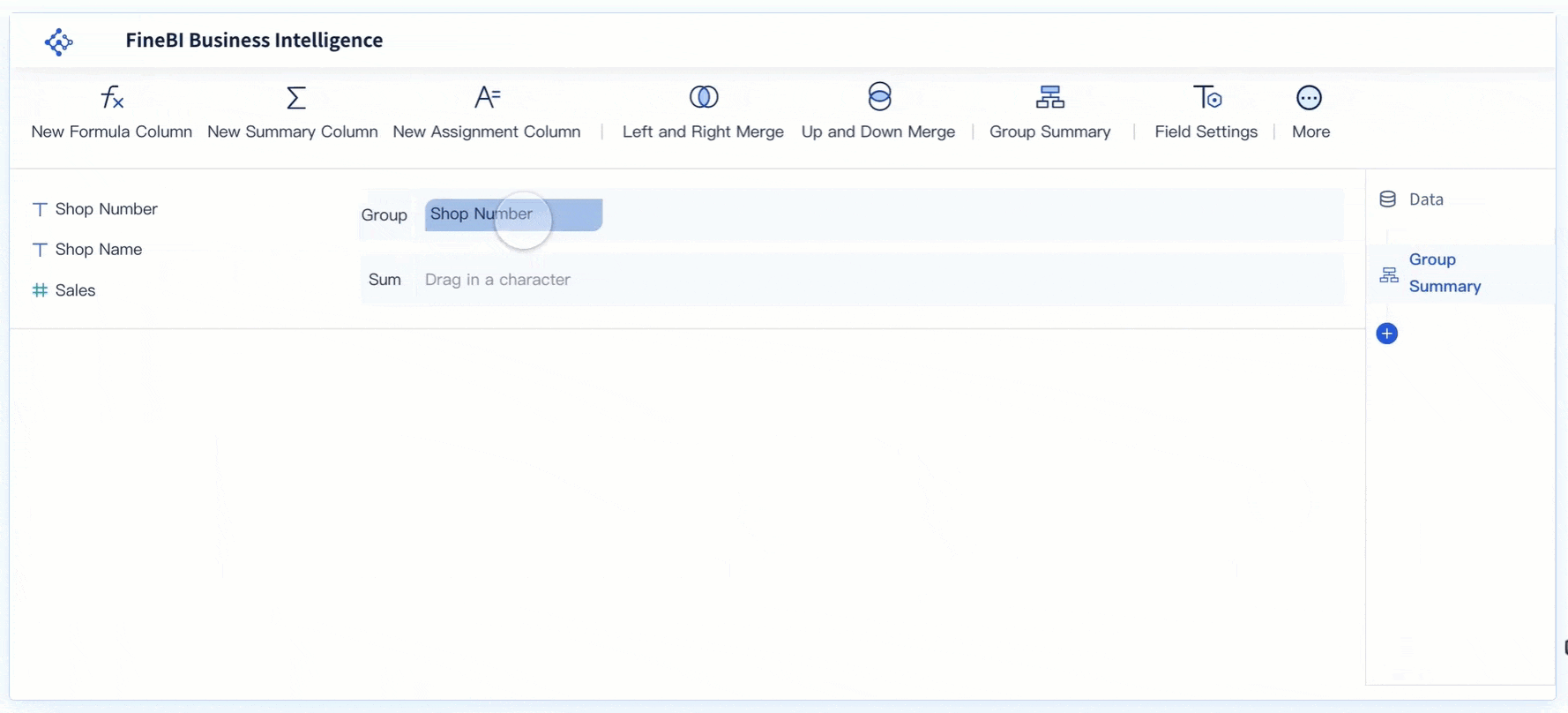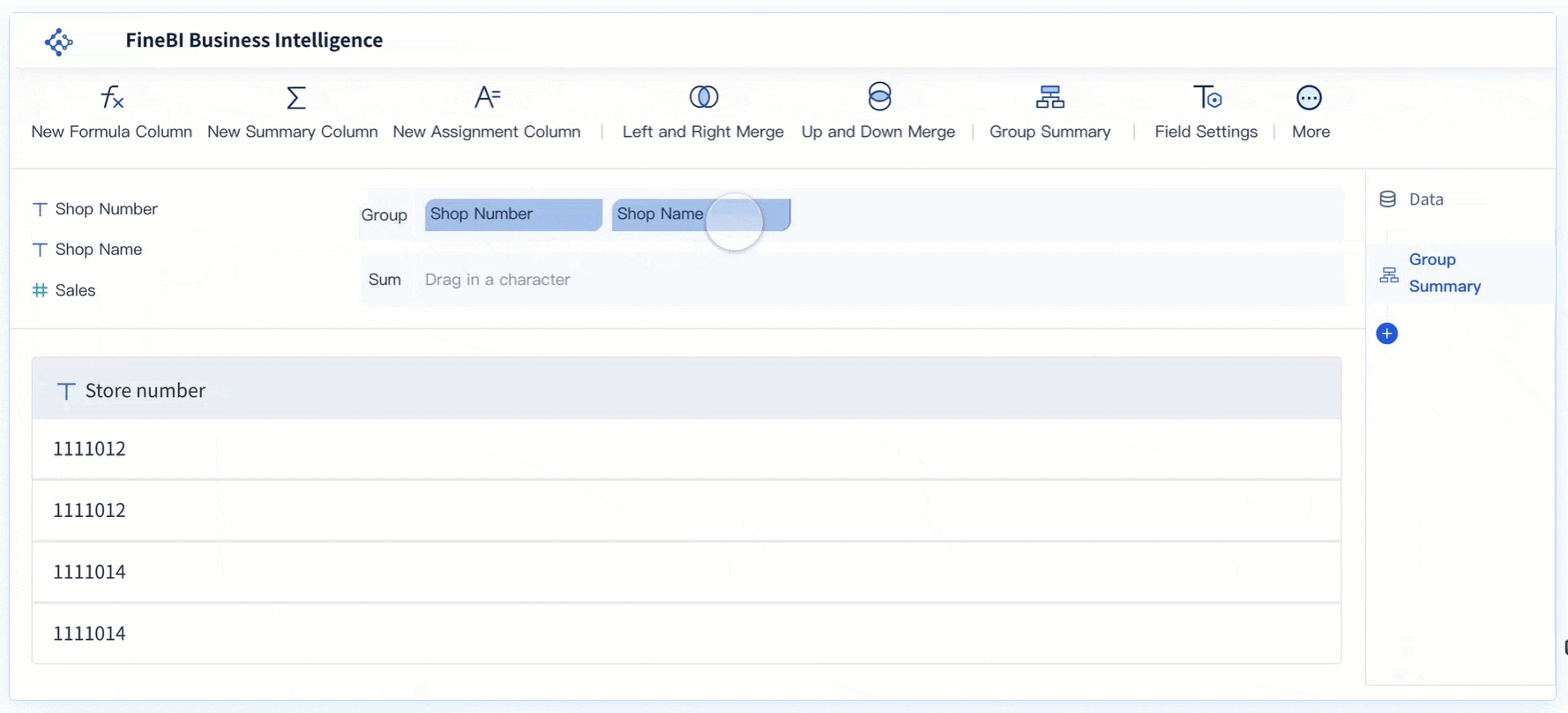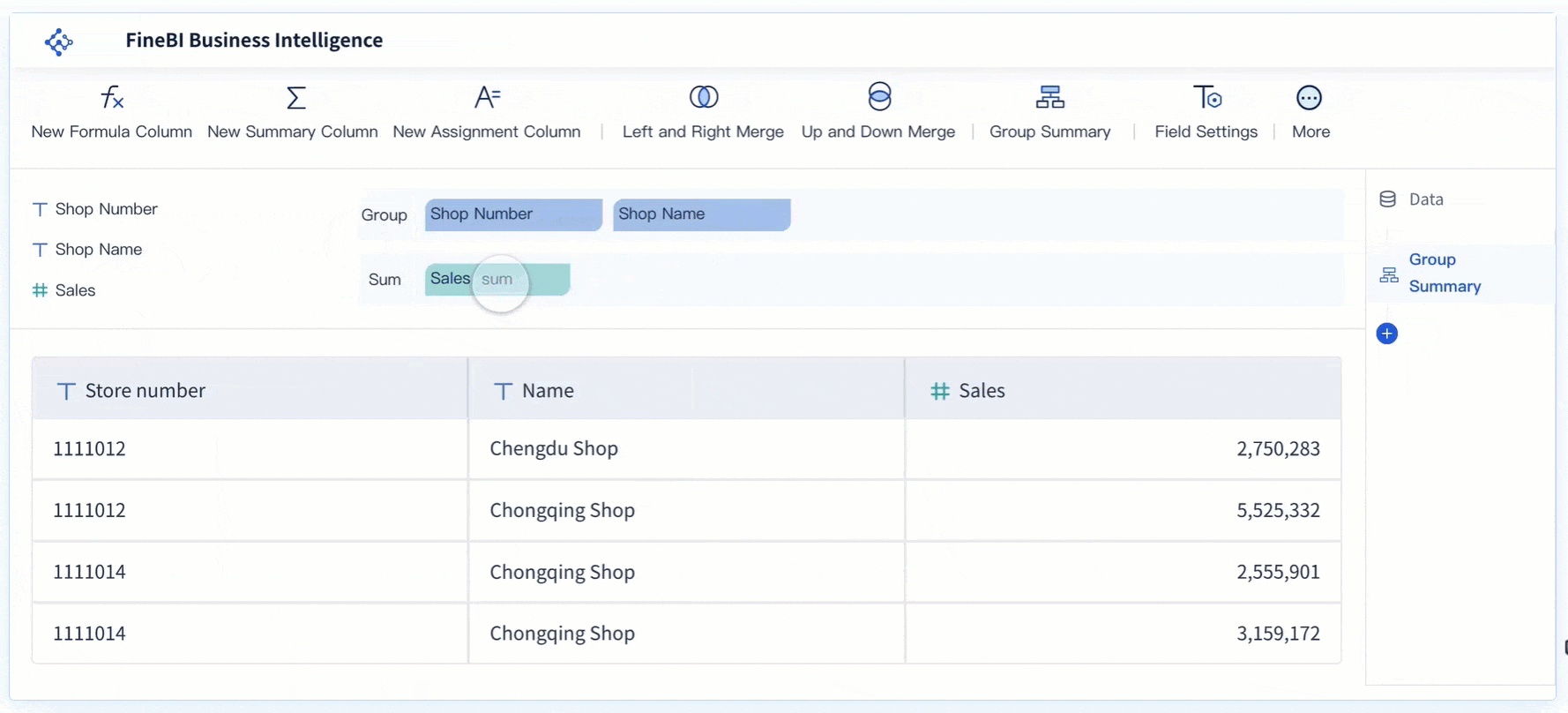
FineBI for Secure Data Analysis
FineBI empowers you to perform secure data analysis with ease. This self-service business intelligence software enables you to connect, analyze, and share data across your organization. FineBI transforms raw data into insightful visualizations, helping you track key performance indicators and identify trends. Its high-performance computing engine can process massive datasets, supporting real-time analysis and boosting productivity. With FineBI, you can ensure that your data analysis processes remain secure and efficient, providing valuable insights for strategic decision-making.
"FanRuan's solutions offer a comprehensive approach to data confidentiality, combining robust security measures with user-friendly interfaces."
By leveraging FanRuan's solutions, you can enhance data confidentiality in your business. These tools not only protect sensitive information but also improve overall efficiency, allowing you to focus on what matters most—growing your business.
To ensure data confidentiality, you must take several key steps. First, identify and classify your data to understand its sensitivity. Implement robust access controls and encryption methods to protect it. Develop comprehensive data confidentiality policies and educate your employees on best practices. Regular audits and updates to your security measures are crucial.
"Data protection is an ongoing effort. Continuously reassess security measures, adapt to new threats, and update strategies."
Adopt a proactive approach to data protection. Stay informed about evolving threats and regulations. By doing so, you not only safeguard sensitive information but also build trust with your customers.
FAQ
Data confidentiality refers to the protection of sensitive information from unauthorized access. It ensures that only authorized individuals can view or use specific data. Maintaining confidentiality helps prevent data breaches and protects your business's reputation.
Data breaches can lead to financial losses and damage your reputation. Protecting data confidentiality helps you comply with legal obligations and build trust with customers. It also safeguards intellectual property and sensitive information, ensuring your business remains competitive.
You can ensure data confidentiality by implementing strong access controls and encryption methods. Regularly update security software and conduct audits to identify vulnerabilities. Educate employees on data security best practices to reduce the risk of unauthorized access.
Employees serve as the first line of defense against data breaches. Training them on data security best practices is crucial. Encourage them to report security incidents promptly and reward good security practices to foster a security-conscious culture.
Regulations like GDPR and CCPA set standards for handling personal data. They require you to protect data from unauthorized access and ensure transparency in data usage. Non-compliance can result in hefty fines, making it essential to align your data practices with these regulations.
Businesses often face challenges such as unauthorized access, data breaches, and compliance with regulations. Keeping up with evolving threats and ensuring employee awareness can also be challenging. Regular audits and updates to security measures can help address these issues.
FanRuan offers tools like FineDataLink, FineReport, and FineBI to enhance data confidentiality. These solutions provide secure data integration, reporting, and analysis, ensuring that your sensitive information remains protected. They also streamline data management processes, improving overall efficiency.
Continue Reading About Data Confidentiality
2025 Data Pipeline Examples: Learn & Master with Ease!
Unlock 2025’s Data Pipeline Examples! Discover how they automate data flow, boost quality, and deliver real-time insights for smarter business decisions.
Howard
Feb 24, 2025
2025's Best Data Validation Tools: Top 7 Picks
Explore the top 7 data validation tools of 2025, featuring key features, benefits, user experiences, and pricing to ensure accurate and reliable data.
Howard
Aug 09, 2024
2025 Best Data Integration Solutions and Selection Guide
Explore top data integration solutions for 2025, enhancing data management and operational efficiency with leading platforms like Fivetran and Talend.
Howard
Dec 19, 2024
Best Data Integration Platforms to Use in 2025
Explore the best data integration platforms for 2025, including cloud-based, on-premises, and hybrid solutions. Learn about key features, benefits, and top players.
Howard
Jun 20, 2024
Best Data Management Tools of 2025
Explore the best data management tools of 2025, including FineDataLink, Talend, and Snowflake. Learn about their features, pros, cons, and ideal use cases.
Howard
Aug 04, 2024
Best Data Integration Vendors for Seamless Workflows
Discover the top 20 data integration vendors of 2025 for seamless workflows. Compare tools like Talend, AWS Glue, and Fivetran to optimize your data processes.
Howard
Jan 22, 2025


