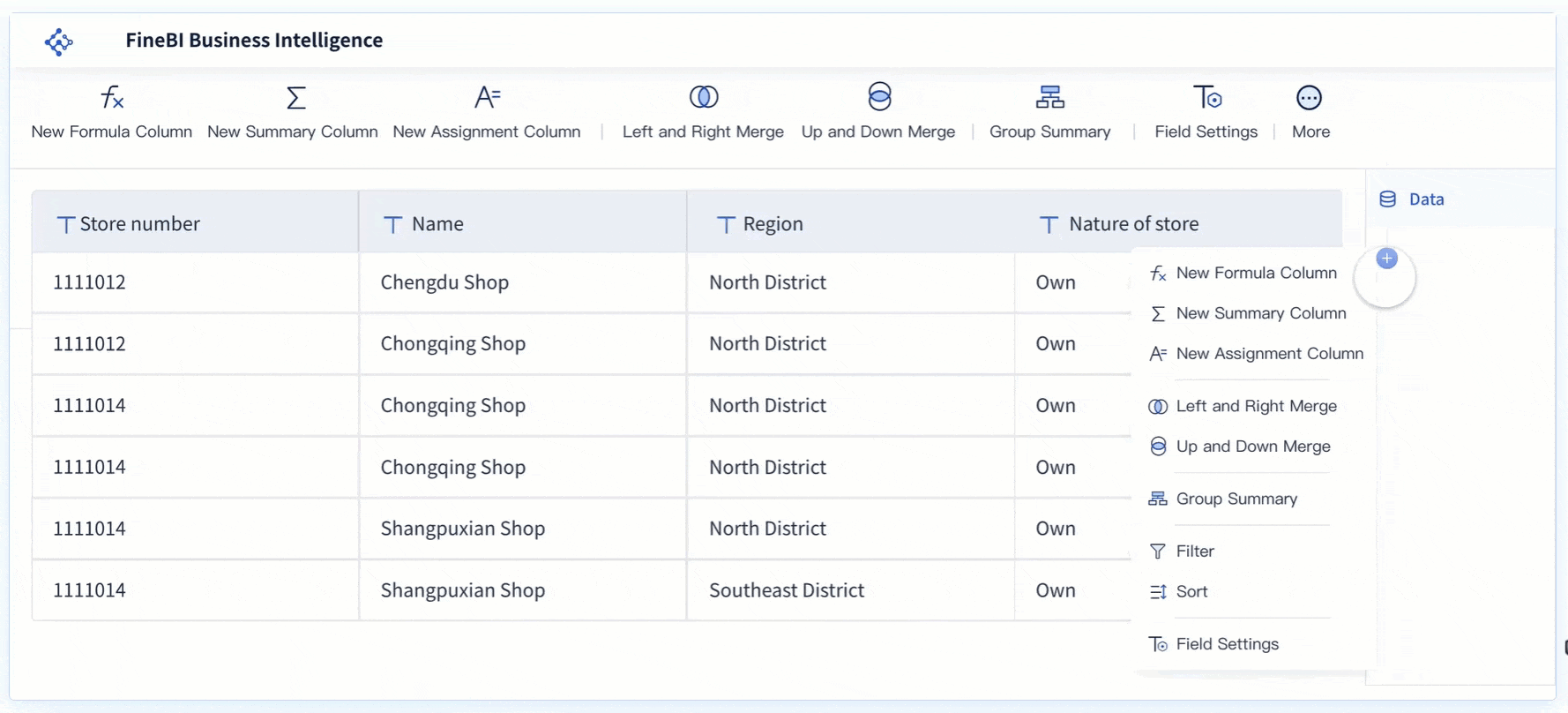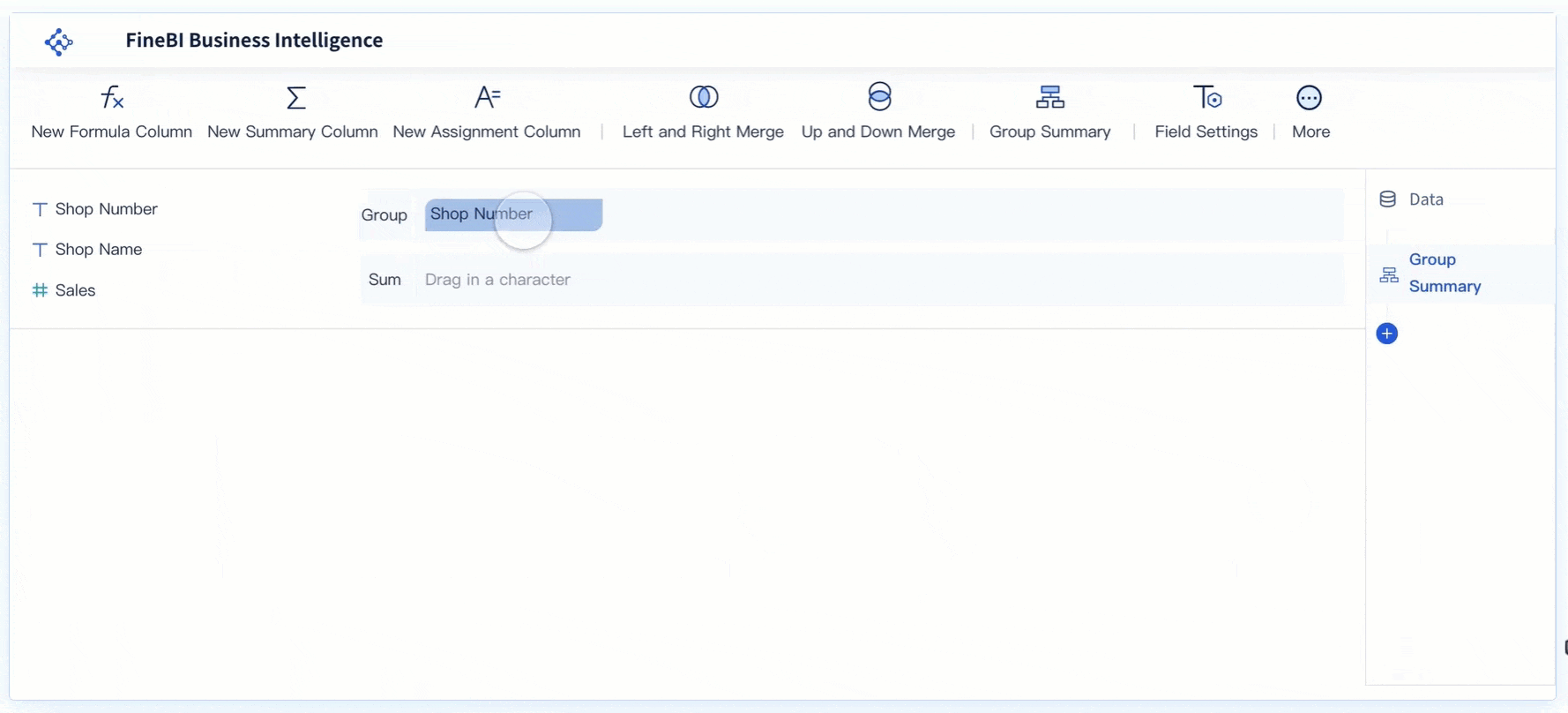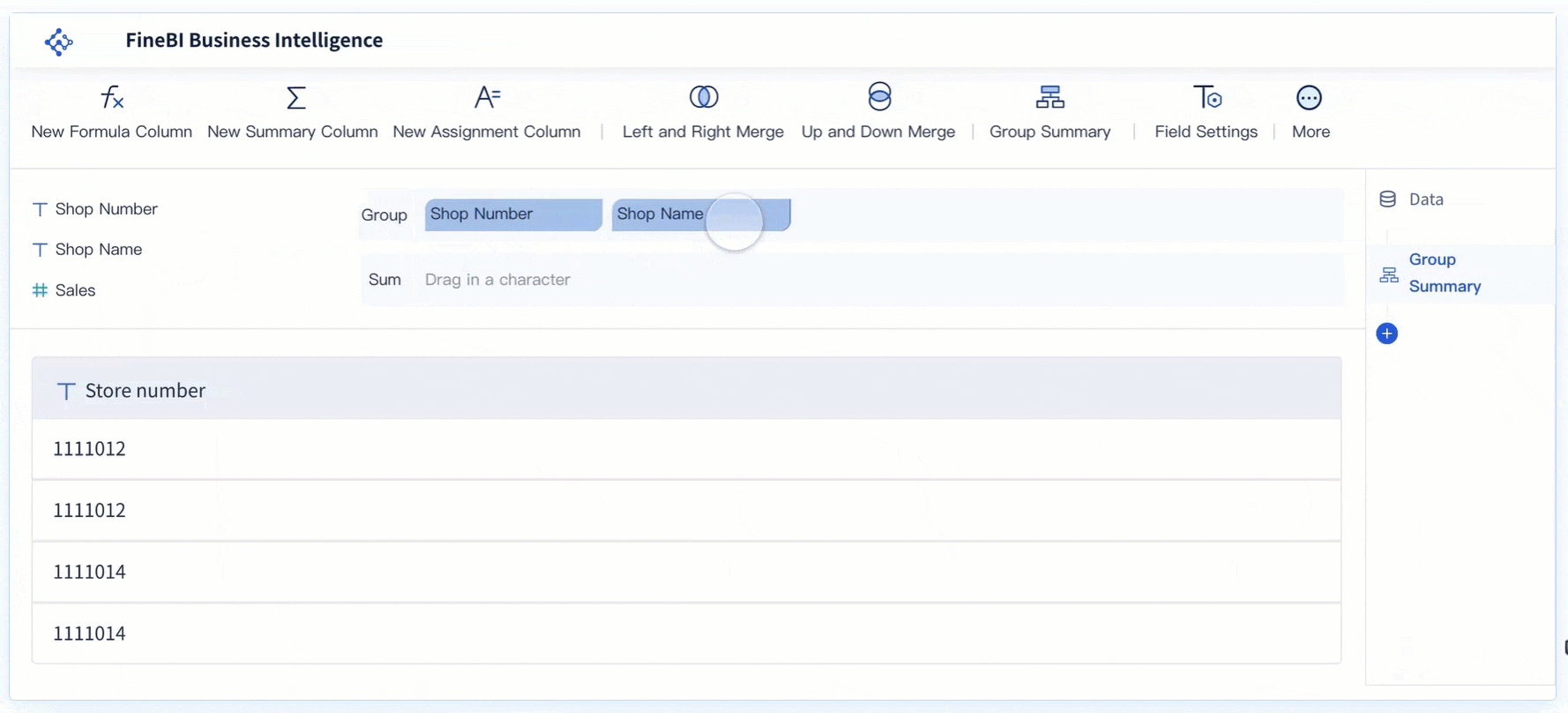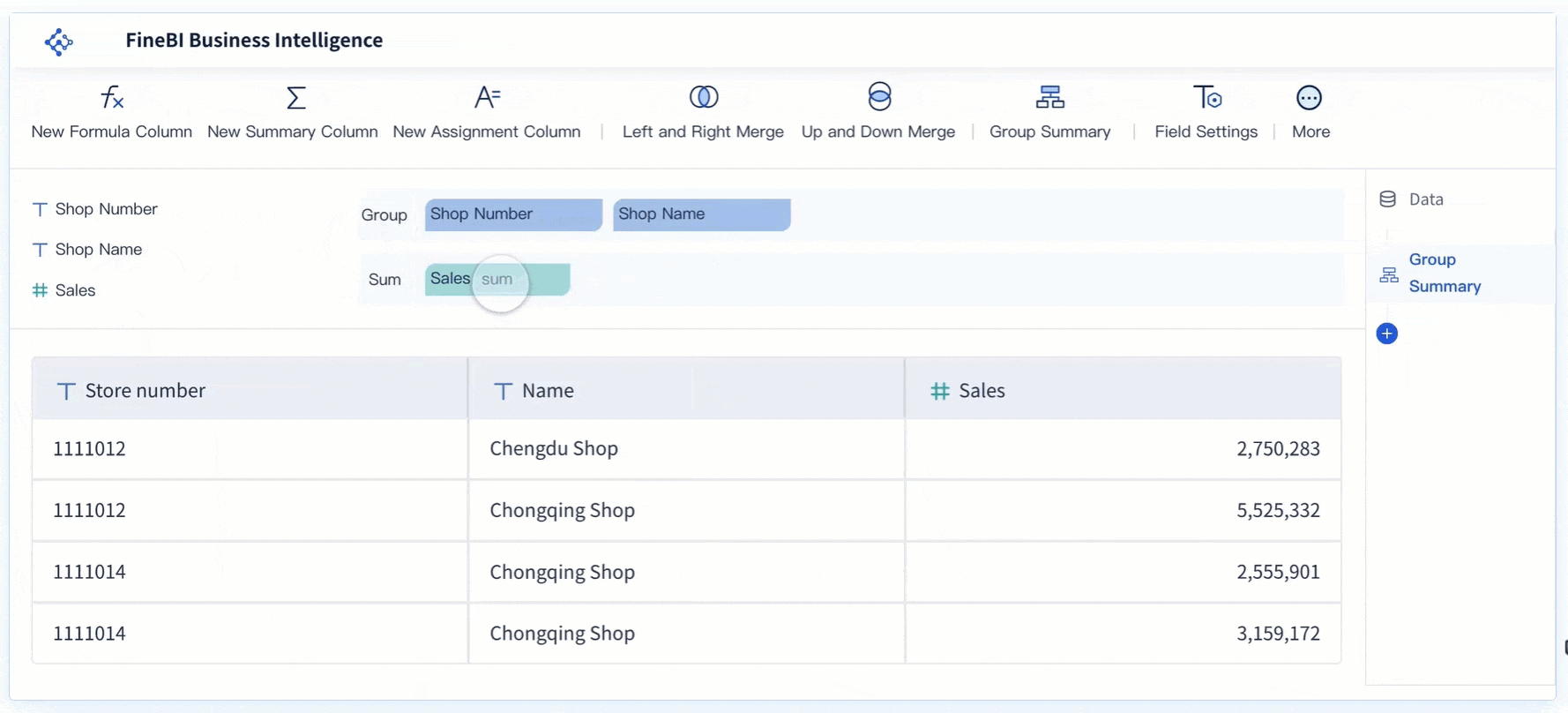
Security management means putting in place processes and policies to protect your information, assets, and people from threats. You face risks every day—at work and at home—when security is not a priority. Consider these facts:
| Statistic | Value |
|---|---|
| Data breaches increase (2013-2022) | 200% |
| Personal records compromised (2021-2023) | 2.6 billion |
| Average cost per breach (2024) | $4.88 million |
| Human factor in breaches | 68% |
If you neglect security, you risk financial loss, data leaks, and a damaged reputation. Security management supports business continuity and builds trust by making sure you stay resilient and communicate clearly during any crisis.
Security management means protecting your organization’s assets, information, and people from threats. You use security management to create policies and procedures that keep your business safe. This approach helps you identify risks, set up controls, and respond to incidents quickly.
You can see how experts define security management in different ways. Here is a table that shows some common definitions:
| Definition | Description |
|---|---|
| Security Management | The main purpose is to protect the enterprise’s assets from identified threats, both internal and external. It involves creating policies and procedures for security strategy implementation. |
| Security Management | Processes that enable an organizational structure and technology to protect IT operations and assets from threats, ensuring confidentiality, integrity, and availability. |
| Security Management | Involves applying risk management principles to security threats, including identifying threats, assessing controls, and prioritizing risks. |
| Security Management | A structured approach to protecting people, physical assets, and digital infrastructure, involving policy development and risk reduction strategies. |
You need a strong security management strategy to keep your business running smoothly and to build trust with your customers.
A good security management strategy includes several important parts. You should focus on these key components:
These components work together to create a complete security management system. You need to address all types of security management, including physical, information, personnel, and cybersecurity.
Many people believe myths about security management. These ideas can put your organization at risk. Here are some of the most common misconceptions:
You need to challenge these myths and understand that security management is an ongoing process. You must update your security management strategy regularly and involve everyone in your organization.

Security management means creating a set of rules, processes, and actions to protect your organization from threats. You use security management to make sure your information, assets, and people stay safe. This approach helps you set up a security policy, apply security controls, and manage risks before problems occur.
You need security management because threats are everywhere. Cybersecurity incidents, data leaks, and physical breaches can happen at any time. A strong security policy and effective security controls help you prevent these issues. Security program management gives you a clear plan to follow, so you can respond quickly and keep your business running.
If you ignore security management, you put your organization at risk. Weak security policy and missing security controls can lead to serious problems. You may face financial loss, legal trouble, and a damaged reputation. Many companies have learned this lesson the hard way.
| Consequence Type | Description |
|---|---|
| Business Reputation and ROI | Negative impacts on a company's reputation and return on investment due to cybersecurity incidents. |
| National Security Issues | Broader implications for national security stemming from poor security management. |
| Widespread Consequences | Extensive repercussions for operational technology companies affected by cyber incidents. |
You can see the impact in real-world cases:
Security breaches do not just affect your data. They can disrupt your operations and harm your customers. For example:
If you do not have a strong security policy or effective security controls, you risk losing your customers and your business. Security program management helps you avoid these outcomes by making sure you address risks before they become crises.
When you invest in security management, you protect your organization from threats and build trust with your customers. A strong security policy and well-designed security controls give you many advantages.
| Benefit | Description |
|---|---|
| Improved Compliance | Organizations can meet regulatory requirements more effectively. |
| Reduced Risk of Data Breaches | Proactive measures decrease the likelihood of breaches and attacks. |
| Enhanced Customer Trust | Strong security practices build confidence among customers. |
| Improved Reputation | Organizations are viewed more favorably when they prioritize security. |
| Increased Efficiency | Streamlined processes lead to better resource management. |
| Better Risk Assessment | Organizations can identify and prioritize risks more effectively. |
| Improved Adaptability to Change | Organizations can respond more swiftly to new security challenges. |
You also gain these benefits:
Security management also helps you meet legal and regulatory requirements. Many risk and compliance professionals now focus on strategic security program management, not just basic compliance. In fact:
If you fail to comply, you pay a high price. Breaches linked to non-compliance cost an average of $220,000 more. Organizations with high non-compliance levels face an average cost of $5.05 million due to data breaches.
You can see the value of security management in action at Founder Securities. This leading financial services company needed to improve its security program management and data-driven decision-making. The company faced challenges with operational efficiency and secure data access.
Founder Securities chose FineBI to support its security management goals. FineBI helped the company set up a strong security policy and apply security controls across its operations. Over 2,000 employees gained secure, independent access to data. This improved workflows and allowed teams to make faster, safer decisions.
During a major merger, Founder Securities used FineBI to migrate 50,000 user accounts securely. The company segmented clients, managed risks, and monitored data in real time. Security program management ensured that sensitive information stayed protected and that business operations continued without disruption.
FineBI’s features, such as role-based access control and audit trails, supported the company’s security policy. These security controls allowed Founder Securities to track user activity and prevent unauthorized access. The company built trust with its customers and met regulatory requirements.
Founder Securities now uses security management as a foundation for growth. The company’s experience shows that strong security program management, supported by the right tools, leads to better outcomes. You can achieve the same results by making security management a priority in your organization.

Information security management is a core part of security management. You use information security management to protect your digital assets, such as customer data, business records, and intellectual property. This process involves setting up security controls, monitoring access, and ensuring that only authorized users can view or change sensitive information. Security management gives you a framework to identify risks, apply security controls, and respond to incidents quickly.
You need information security management because digital threats are always evolving. Hackers, insider threats, and accidental data leaks can all put your organization at risk. Security management helps you create policies and procedures that keep your information safe. You must focus on data protection, regulatory compliance, and the ability to recover from incidents. Security controls, such as access restrictions and audit trails, form the backbone of a strong information security management program.
Data governance is the foundation of effective information security management. You need clear rules and responsibilities for managing data. FineBI supports your data governance efforts by providing tools that help you organize, monitor, and protect your information. The platform aligns with the core principles of data governance, which include:
FineBI makes it easier for you to manage these principles. You can connect to multiple data sources, set up validation rules, and monitor data quality. The platform helps you document your policies and track changes, which supports both security management and information security management goals.
Tip: Strong data governance reduces the risk of errors, data loss, and unauthorized access. You build trust with customers and regulators when you show that your data is well managed.

Role-based access control (RBAC) is a key security control in information security management. You use RBAC to limit who can see or change specific data. FineBI lets you assign permissions based on job roles, so each user only gets access to the information they need.
To implement RBAC effectively with business intelligence tools like FineBI, follow these best practices:
FineBI's RBAC features help you enforce these best practices. You can assign, review, and update permissions easily, which strengthens your overall security management.
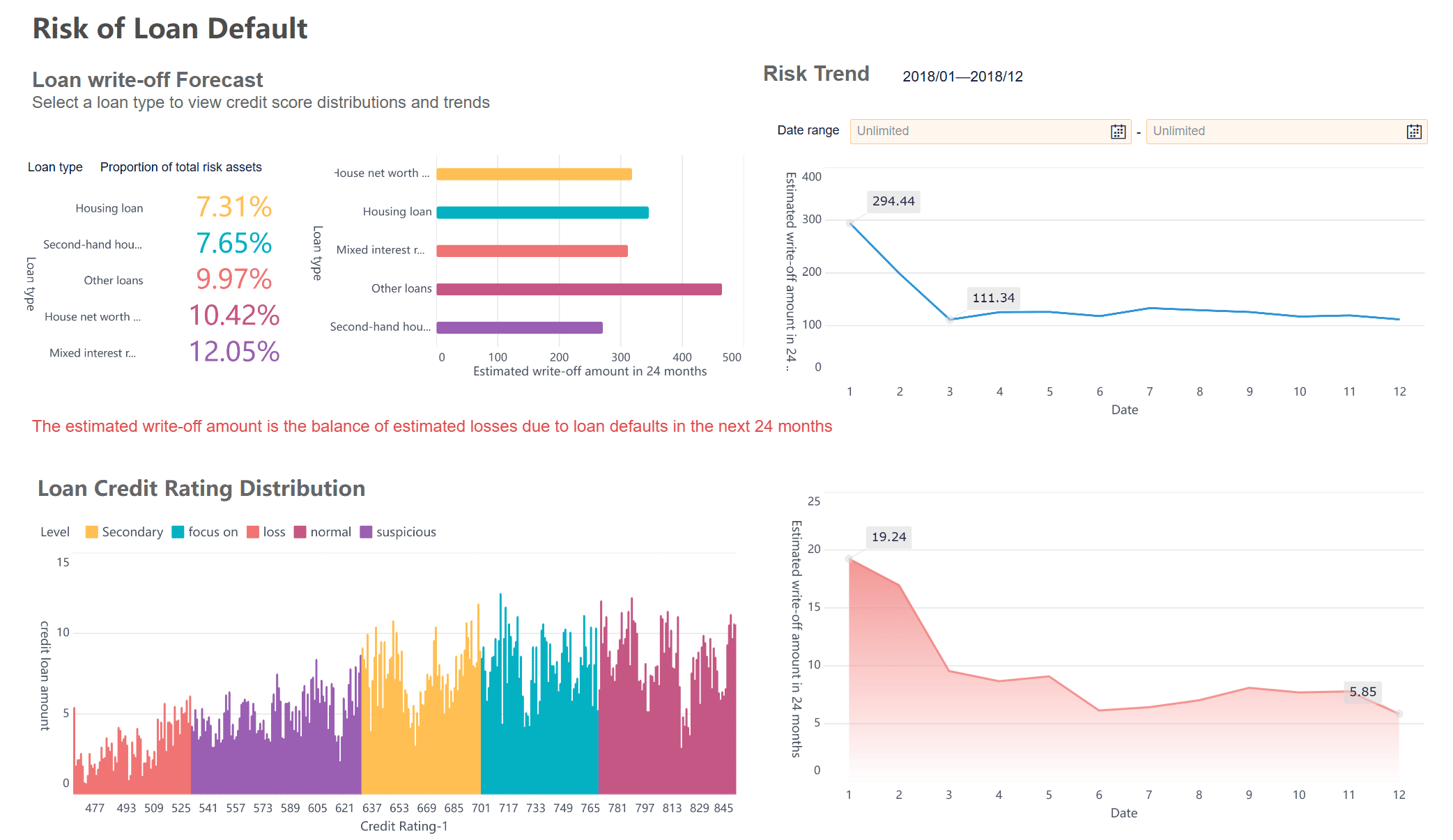
Compliance is a major concern in information security management. You must follow laws and regulations that require you to protect sensitive data and prove that you have effective security controls in place. FineBI supports compliance by offering audit logging, role-based access control, and row-level security.
FineBI’s security and governance controls align with regulatory requirements. You can manage sensitive data, monitor access, and ensure that your organization meets industry standards. This approach to information security management protects your digital assets and helps you avoid costly penalties.
Note: Regularly review your audit trails and update your security controls to keep up with new threats and regulations. This proactive approach strengthens your security management and builds trust with stakeholders.
Information security management is not just about technology. You need a clear strategy, strong security controls, and the right tools to protect your organization. FineBI gives you the features you need to manage data governance, access control, and compliance—all within a single platform. By focusing on these areas, you can reduce risks, meet regulatory requirements, and ensure the ongoing security of your digital assets.

Security management in modern organizations means building a strong defense against digital threats. You use security management to create rules, processes, and security controls that protect your systems, data, and people from cyberattacks. This approach helps you identify risks, set up security management solutions, and respond quickly to incidents.
You need security management because cyber threats continue to grow in number and complexity. Without effective security controls and a clear cybersecurity strategy, your organization faces increased vulnerabilities. Security management solutions help you stay ahead of attackers and keep your business safe.
Modern organizations face a wide range of cybersecurity threats. You must understand these risks to build effective security management solutions. The table below shows the most significant threats:
| Cybersecurity Threat | Description |
|---|---|
| Social Engineering | Exploits human error; 68% of breaches involve non-intentional human interaction. |
| Third-party Exposure | Attacks through less secure partners; 29% of breaches come from third parties. |
| Ransomware | Blocks access to files until a ransom is paid; recovery costs keep rising. |
| State Sponsored Attacks | Nations target critical infrastructure, often for political or economic gain. |
| Insider Threats | Risks from employees or contractors, intentional or accidental, often hard to detect. |
| Drive-by Cyberattacks | Malware downloads silently when users visit compromised websites. |
| Poor Cyber Hygiene | Bad habits and lack of education increase vulnerability to attacks. |
You also see the frequency of attacks rising. For example:
| Year | Percentage of Organizations Affected by Ransomware |
|---|---|
| 2018 | 55.1% |
| 2023 | 72.7% |
| Year | Number of Malware Attacks (in billions) |
|---|---|
| 2022 | 5.51 |
| 2023 | 6.06 |
| Year | Daily Spam Emails (in billions) |
|---|---|
| 2023 | 3.4 |
These numbers show why you need strong security controls and ongoing cybersecurity management.
FineBI offers advanced security features to help you defend against common cyber threats. You can rely on these security controls to protect your data and users:
| Security Feature | Description |
|---|---|
| XSS Attack Protection | Blocks Cross-Site Scripting by adding a response header that stops the page from loading if detected. |
| Click Attack Protection | Prevents clickjacking by restricting the embedding of pages in iframes from other origins. |
You use these features as part of your security management solutions to reduce vulnerabilities and improve threat detection and response. FineBI’s security controls work alongside other tools to create a layered defense.
You can strengthen your cybersecurity management by following industry-recommended best practices. These actions help you build a safer environment and support your security management goals:
| Best Practice | Description |
|---|---|
| Segregate and Control Internal Data | Isolate critical systems and limit third-party access. |
| Apply the Principle of Least Privilege | Give users only the access they need, using tiered models for admin accounts. |
| Apply Updates Regularly | Patch all systems quickly, focusing on known vulnerabilities. |
| Take Preventative Measures | Use mitigation tools and assess your cyber maturity. |
| Be Diligent with Logging and Monitoring | Keep important logs for at least six months to help with incident detection. |
| Deploy Multi-Factor Authentication | Add extra security for remote access and audit account privileges often. |
You measure the success of these best practices by tracking how quickly you patch vulnerabilities, monitoring reductions in security incidents, and checking adherence to service agreements. You also align your program with frameworks like NIST CSF and gather feedback from your team to improve your security management solutions.
Tip: Regularly review your security controls and update your cybersecurity management plan. This proactive approach helps you stay ahead of new threats and keeps your organization secure.
Security management means creating a structured approach to protect your organization’s information, assets, and people from threats. You use security management to set up policies, procedures, and controls that help you identify risks, prevent incidents, and respond quickly when problems occur. This process ensures that your security measures stay effective as your organization grows and faces new challenges.
You need to review your current security management regularly. This helps you find weaknesses and improve your defenses. By assessing your security, you can make informed decisions and keep your organization safe from evolving threats.
Start by evaluating your current security posture. Use a mix of methods to get a clear picture:
| Method | Description |
|---|---|
| Certifications | External assessments against recognized standards (e.g., ISO 27001) to validate security measures. |
| Internal Audits | Systematic evaluations to ensure compliance with policies and identify non-conformities. |
| Information Security Metrics | Quantitative measures to monitor the effectiveness of security measures and inform decisions. |
| Management Reviews | Periodic evaluations by top management to assess overall security progress and resource allocation. |
| Application Security Testing | Technological assessments to identify vulnerabilities in systems and applications. |
| Employee Awareness Assessments | Evaluations of employee understanding and compliance with security policies in daily operations. |
Common gaps often appear during these assessments. You may find issues such as inadequate security policies, outdated risk assessments, weak access controls, and lack of employee training. Addressing these gaps is essential for strong security management.
You can improve your security by following proven best practices:
Make your security policies clear and accessible. Assign ownership for each process and conduct regular audits. Encourage open communication about security issues and create a culture of continuous improvement.
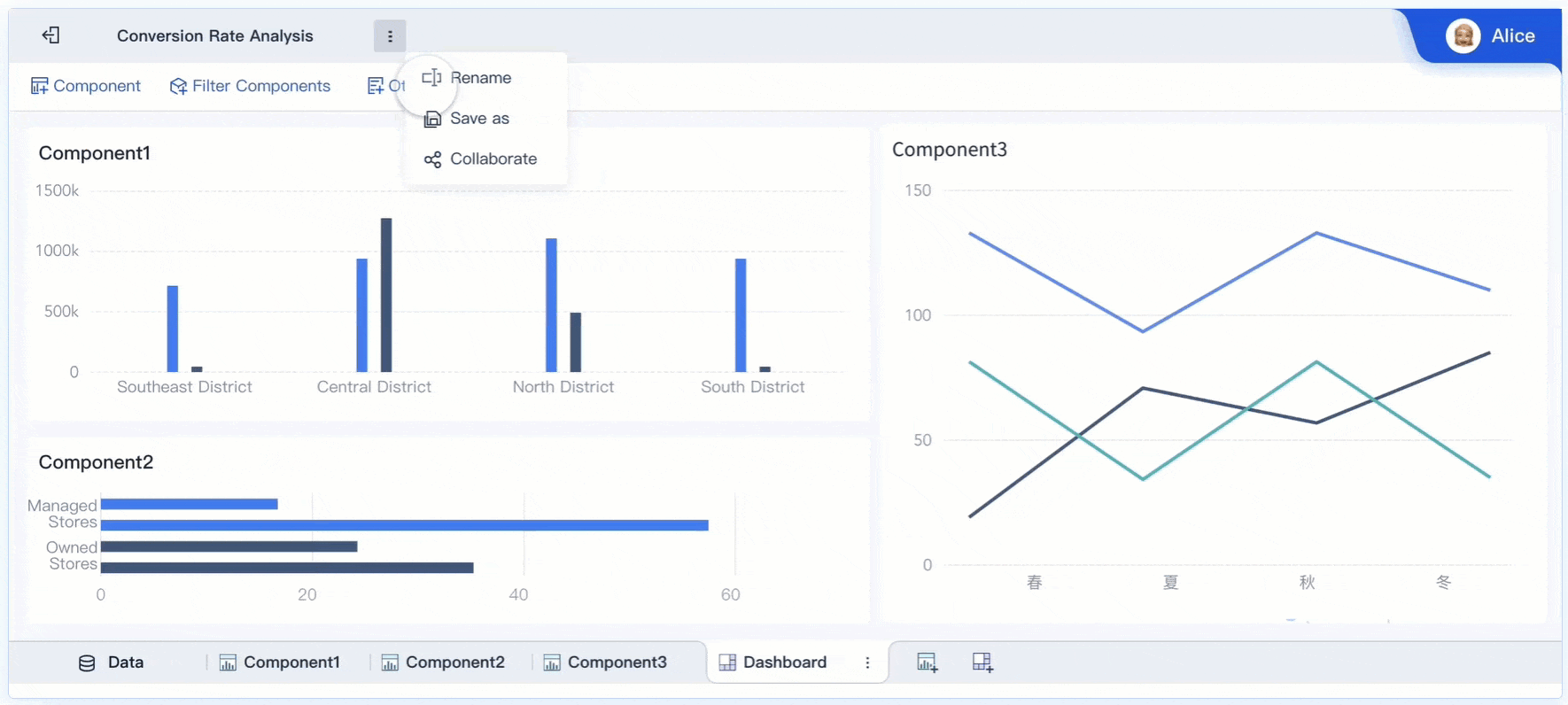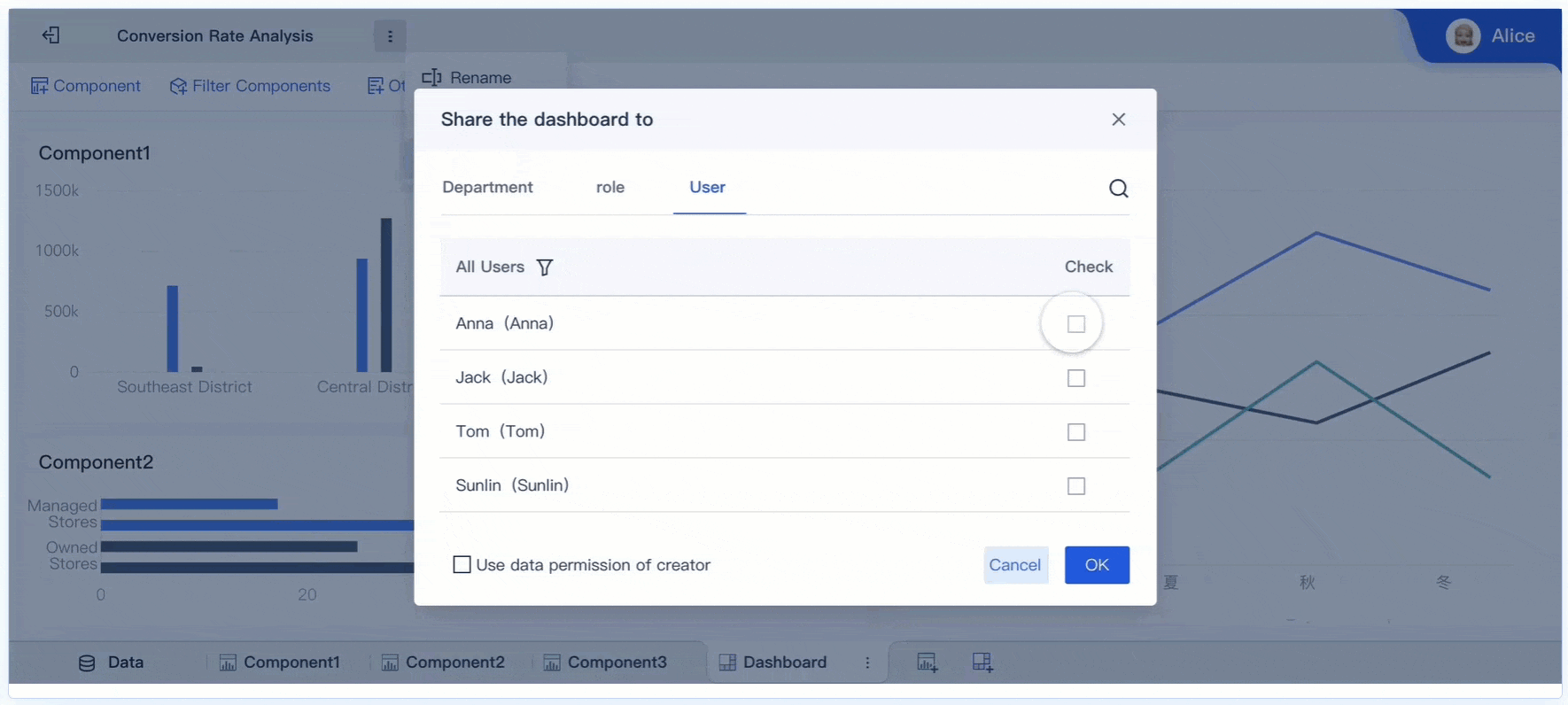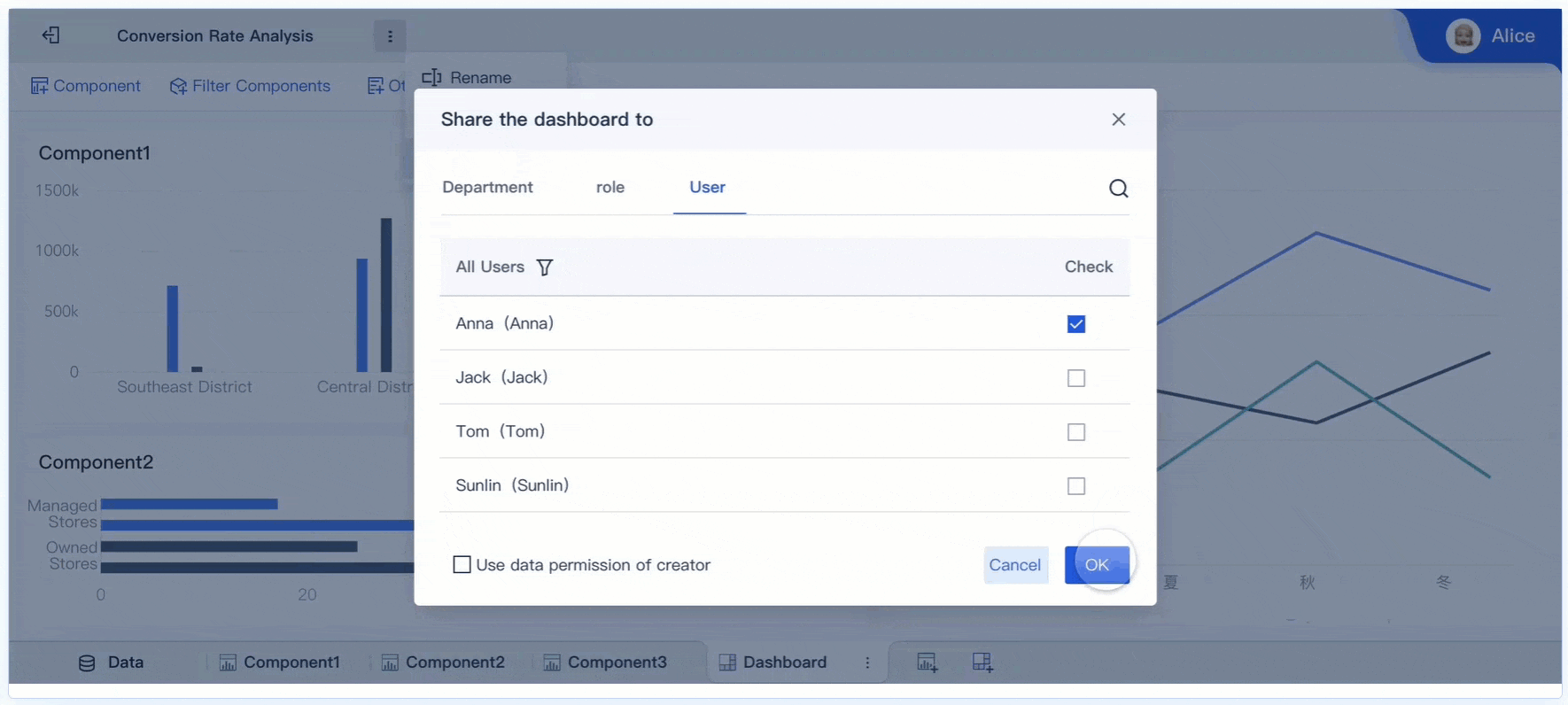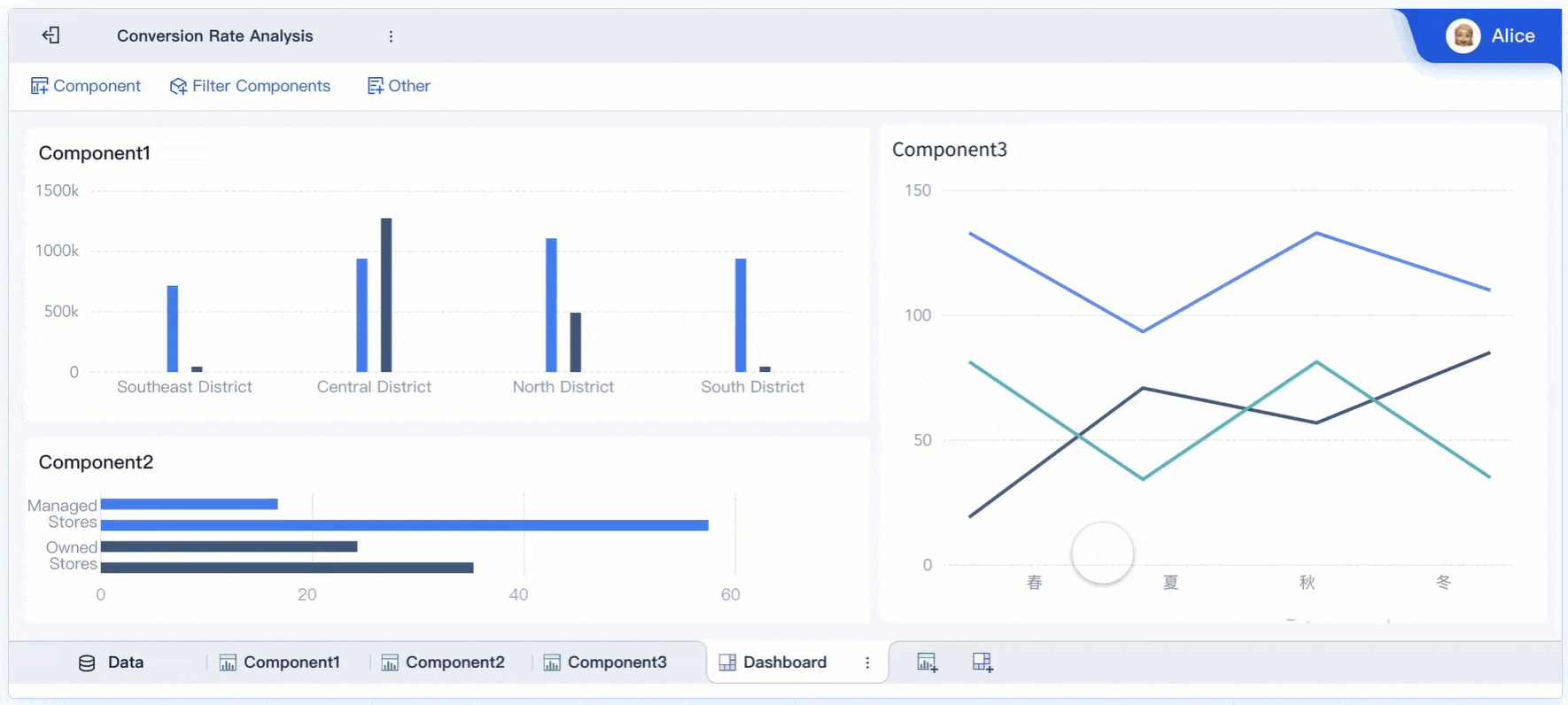
Modern tools like FineBI help you strengthen your security management. FineBI supports role-based access control, audit trails, and data governance. You can monitor user activity, enforce security policies, and ensure compliance with regulations. FineBI also makes it easier to identify risks and respond to incidents quickly. By using advanced analytics and automation, you can streamline your security processes and protect your organization more effectively.
Tip: Regularly update your security tools and review your policies to stay ahead of new threats. Consistent improvement keeps your security management strong and reliable.
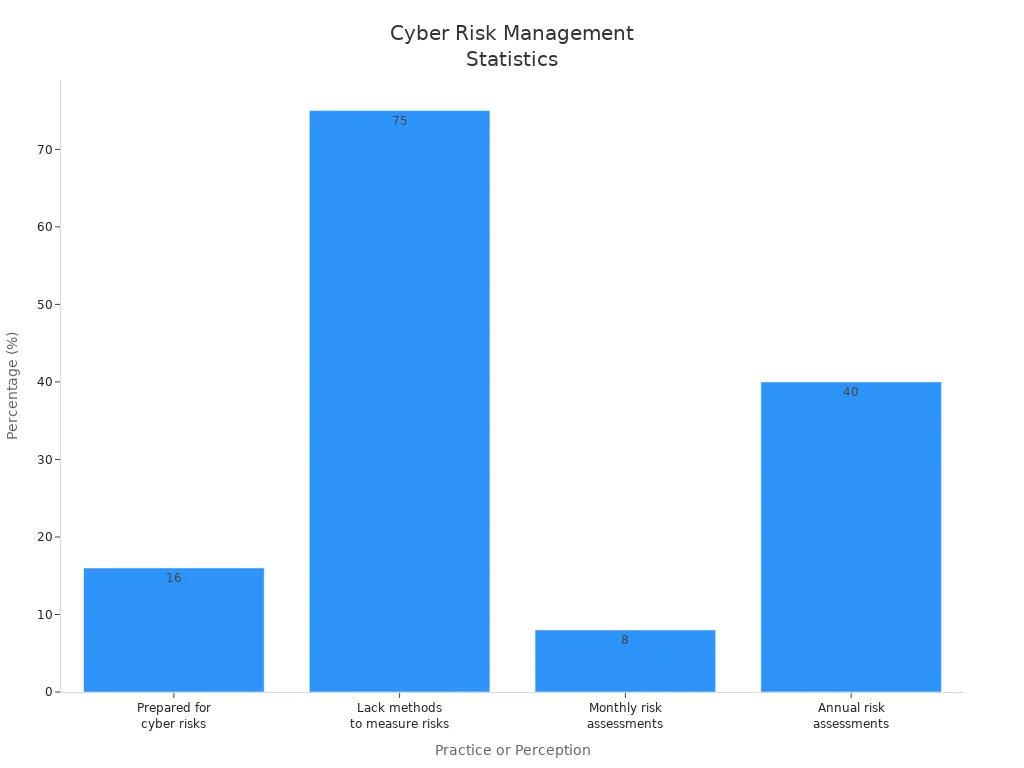
You face new security threats every day. Security management gives you the structure to protect your data, assets, and reputation. Only 16% of executives feel prepared for cyber risks, while 75% struggle to measure and understand them. Most organizations assess cyber risks too rarely, as shown below:
| Statistic | Description |
|---|---|
| 16% | Executives feel their organizations are adequately prepared for cyber risks. |
| 75% | Executives report lacking effective methods to measure and understand cyber risks. |
| 8% | Organizations conduct monthly cyber risk assessments. |
| 40% | Organizations perform cyber risk assessments just once per year. |
Neglecting security can lead to costly breaches, as seen with SolarWinds, Target, and Equifax. You can avoid these outcomes by making security management a priority. Start by reviewing your current security practices and consider solutions like FineBI to strengthen your defenses. Stay alert, keep learning, and make security a daily habit.

The Author
Lewis
Senior Data Analyst at FanRuan
Related Articles
What is a data management platform in 2025
A data management platform in 2025 centralizes, organizes, and activates business data, enabling smarter decisions and real-time insights across industries.
Howard
Dec 22, 2025

Top 10 Database Management Tools for 2025
See the top 10 database management tools for 2025, comparing features, security, and scalability to help you choose the right solution for your business.
Howard
Dec 17, 2025

Best Data Lake Vendors For Enterprise Needs
Compare top data lake vendors for enterprise needs. See which platforms offer the best scalability, integration, and security for your business.
Howard
Dec 07, 2025