Data protection tools are solutions that secure, monitor, and manage sensitive data to prevent unauthorized access, loss, or misuse.
Here are 10 data protection tools you can try to protect your data:
You face more risks to your business data than ever before. Data protection tools have become essential for keeping your information safe in 2025. You need data loss prevention and privacy tools to meet security standards and follow the law. Over the past five years, more companies have started using data protection solutions for these reasons:
Sensitive data needs strong protection. When you choose a tool, think about your company’s size, your industry, and what kind of data you handle.
You face new risks to sensitive data every year. Attackers use advanced methods to target your business. AI-powered cyber-attacks and deepfake technology make threats harder to spot. Ransomware attacks grow more complex and frequent. Supply chain attacks now affect thousands of organizations. The table below shows the most significant threats projected for 2025:
| Threat Type | Description |
|---|---|
| AI-powered Cyber-Attacks | Cybercriminals use AI to enhance attack sophistication, making them harder to detect. |
| Deepfake Technology | AI-generated fake content that can mislead and manipulate public perception. |
| Malware Threats | Includes various forms of malware, with AI-enhanced variants becoming a primary concern. |
| Ransomware | Attacks are increasing in frequency and sophistication, with a significant year-over-year rise. |
| Supply Chain Attacks | Exploit trusted relationships to breach multiple entities, affecting thousands of organizations. |
| Internet of Things Attacks | Vulnerabilities in connected devices that can be exploited for large-scale attacks. |
| State-sponsored Cyber Activities | Espionage and sabotage operations by nation-states targeting critical infrastructure. |
| Insider Threats | Risks from individuals within organizations misusing their access to systems and data. |
You need top data security tools and dlp solutions to protect sensitive data from these threats. Data loss prevention and data privacy tools help you defend against ransomware and insider risks. Dlp keeps your enterprise data security strong.
You must follow strict privacy compliance rules in 2025. Laws like GDPR, DSA, and state regulations require you to protect sensitive information. Data privacy tools and data privacy software help you automate compliance and meet legal standards. The table below highlights key regulations:
| Regulation | Description | Key Requirements |
|---|---|---|
| GDPR | Governs data collection and processing for EU residents. | Consent, Data Breach Notification, Data Subjects' Rights |
| DSA | Addresses illegal content on online platforms. | Transparency reporting, Content moderation, Cooperation with authorities |
| State Laws | Vary by state, focusing on data protection assessments and children's privacy. | Data protection assessments, Stricter data minimization, Children's privacy regulations |
Data privacy tools and data privacy software locate and classify sensitive data. They record consent and track opt-out requests. These tools automate data access and deletion requests, supporting workflows for multiple privacy laws like hipaa. You need the best data privacy software to keep up with changing rules.
Data loss prevention protects your business from costly data breaches. The average cost of a breach in 2024 reached $4.88 million. Small businesses risk losing 60% of annual revenue and may close within six months after a cyberattack. Healthcare organizations face even higher costs, averaging $9.77 million per breach. Dlp and data protection tools help you avoid financial losses, legal fees, and operational outages.
Tip: Dlp and data privacy software also protect your reputation. Customers and partners trust you more when you use top data security tools and data security applications. Effective dlp ensures you recover quickly from incidents and maintain business continuity.
You need dlp, data privacy tools, and data protection to keep sensitive data safe and your business running.

Choosing the right data protection tools helps you defend your business against data breaches and meet privacy compliance standards. You need solutions that fit your workflows, detect sensitive data accurately, and scale with your organization. The table below shows the criteria used to select these top data security tools for 2025:
| Criteria | Description |
|---|---|
| Integration with existing workflows | Tools should seamlessly fit into current processes. |
| Accuracy in detecting sensitive data | Look for tools with 95%+ accuracy rates. |
| Compliance with regulations | Must adhere to HIPAA, GDPR, SOX, etc. |
| Scalability across the organization | Should be able to grow with the business. |
| Proven enterprise deployments | Evidence of successful use in large organizations. |
You will find that these data protection tools cover a range of use cases, including data loss prevention, data privacy tools, integration, and real-time synchronization. Each tool supports different business sizes and industries. The following table highlights how these solutions address your needs:
| Business Size/Industry | Key Features Addressed | Evidence |
|---|---|---|
| Large Enterprises | Comprehensive data protection for vast data management needs | Large enterprises generate and manage vast amounts of data daily, requiring effective data protection solutions to prevent loss, breaches, and thefts. |
| SMEs | Cost-effective hosted solutions to ensure robust security | Hosted solutions that operate on subscription-based or pay-as-you-go models alleviate the financial burden for SMEs, enabling access to advanced data protection technologies. |
| Various Industries | Flexible deployment options and scalability | The cloud platforms segment captured the largest market share in 2023, offering scalability and flexibility to adjust data protection needs in response to fluctuating data volumes. |
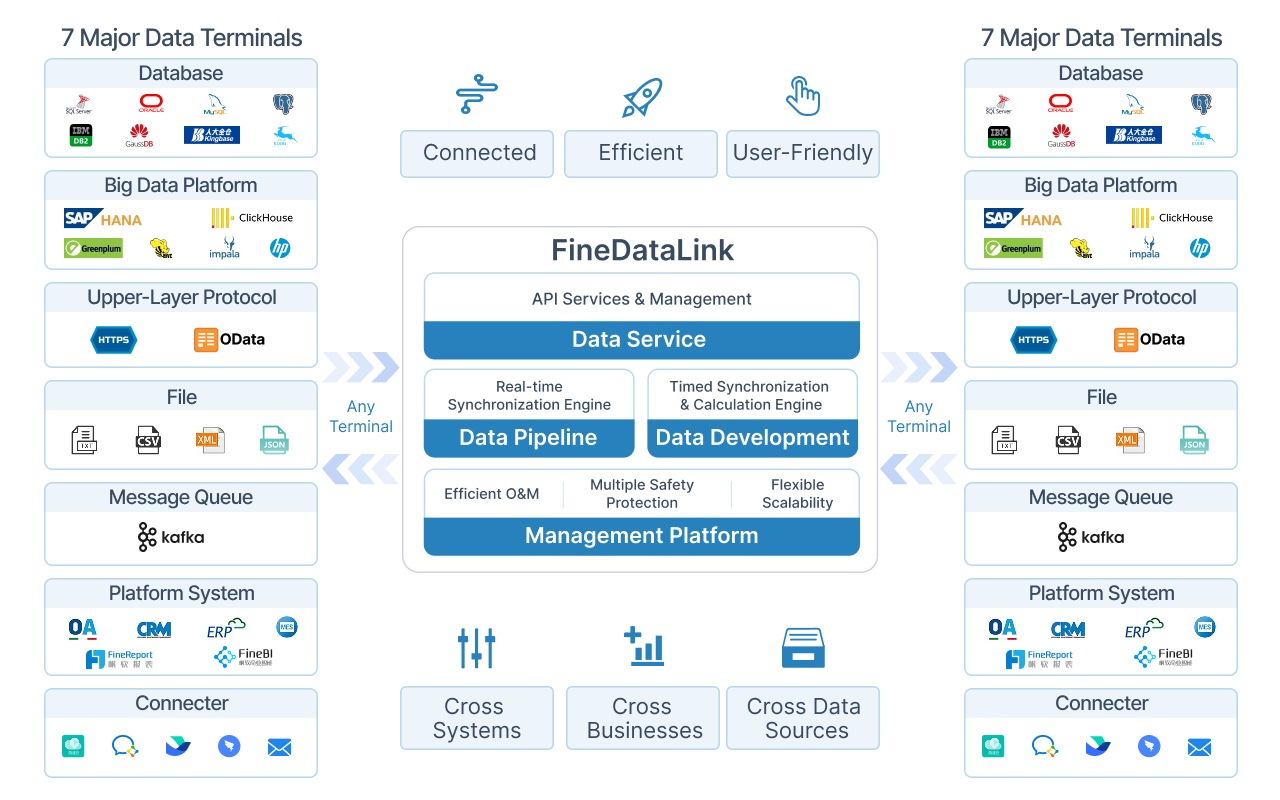
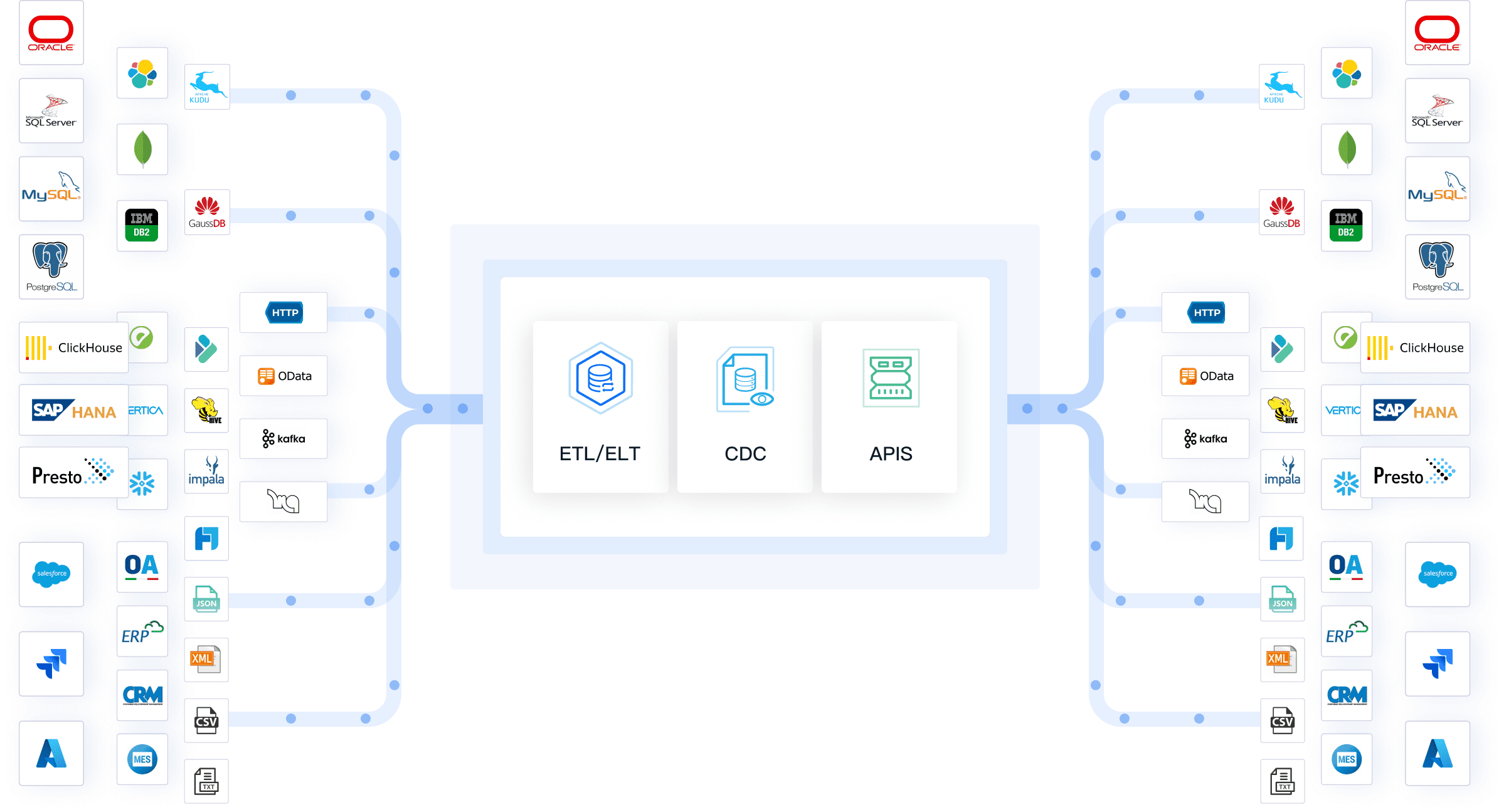
FineDataLink by FanRuan is a modern data integration platform that enables you to synchronize and transform data across multiple sources and systems. You build an efficient data layer for business intelligence and analytics. FineDataLink offers non-intrusive real-time synchronization, so you access business data with minimal latency. You choose from five synchronization methods, including timestamp, trigger, full-table comparison, full-table increment, and log parsing. The high-performance engine improves disaster resistance and supports real-time database backups. FineDataLink automatically synchronizes changes in source table structures. You use APIs to share data between systems and automate compliance workflows. FineDataLink supports over 100 data sources and provides a visual, user-friendly interface.
Website: https://www.fanruan.com/en/finedatalink
| Feature Description | Details |
|---|---|
| Non-intrusive real-time synchronization | Synchronizes data across multiple tables or entire databases, ensuring timely access to business data. |
| Data synchronization methods | Offers five methods: timestamp, trigger, full-table comparison, full-table increment, and log parsing to cater to various scenarios. |
| High-performance synchronization engine | Enhances data warehouse time sensitivity and improves disaster resistance through real-time database backups. |
| Automatic structure synchronization | Automatically synchronizes changes in the source table structure. |
Tip: FineDataLink helps you integrate data from different IT giants, making it a cost-effective solution for businesses with complex data environments.
You need top data security tools like FineDataLink to build a strong foundation for data analytics, business intelligence, and privacy compliance. These data protection tools help you prevent data loss, protect sensitive data, and automate compliance with regulations.
Microsoft Purview DLP gives you advanced data loss prevention for cloud and on-premises environments. You can use AI and machine learning to identify and tag sensitive data across platforms. Deep content inspection helps you reduce false positives. You create policies easily with built-in templates and guided wizards. You apply a single policy across Exchange, SharePoint, and Teams. Flexible enforcement lets you block, warn, or allow actions based on risk. Centralized management and simulation mode help you test policies before going live. Microsoft updates Purview DLP regularly with new templates and classifiers, so your data security stays strong.
| Feature | Description |
|---|---|
| AI and Machine Learning | Automates data protection by identifying and tagging sensitive data across various platforms. |
| Deep Content Inspection | Uses algorithms to validate patterns and detect sensitive content, reducing false positives. |
| Easy Policy Creation | Built-in templates and guided wizards simplify the setup of DLP rules without requiring deep expertise. |
| Unified Deployment | Allows application of a single policy across multiple platforms like Exchange, SharePoint, and Teams. |
| Flexible Enforcement | Offers options to block, warn, or allow actions based on risk levels. |
| Streamlined Management | Centralized management with simulation mode for testing policies and automatic syncing of changes. |
| Continuous Improvement | Regular updates with new templates, classifiers, and AI features to enhance DLP strategies. |
Cyberhaven Data Loss Prevention stands out for its fast SaaS deployment and modern approach to protecting sensitive data. You get a built-in timeline view of incidents, which makes investigation easier. Real-time policy updates let you respond quickly to threats. Cyberhaven combines content inspection and data lineage, reducing false positives by 95%. You protect not only regulated data but also intellectual property and trade secrets. You do not need complex legacy architecture, so you can deploy Cyberhaven in hours.

Website: https://www.cyberhaven.com/product/data-loss-prevention
Symantec DLP remains a leader in enterprise data security. You use it to discover, monitor, and protect sensitive data across endpoints, networks, and cloud applications. Symantec DLP receives recognition from Radicati Group and IDC MarketScape as a top player and pioneer in the DLP market for 2025. You benefit from robust policy enforcement, automated workflows, and advanced reporting. Symantec DLP supports privacy compliance and helps you automate compliance with regulations like HIPAA and GDPR.
Website: https://www.broadcom.com/products/cybersecurity/information-protection/data-loss-prevention
| Award/Recognition | Source | Year |
|---|---|---|
| Top Player | Radicati Group | 2025 |
| Leader | IDC MarketScape | 2025 |
| Pioneer in DLP Market | IDC | 2025 |
Varonis Data Security Platform gives you visibility and control over sensitive data stored in files, emails, and cloud applications. You monitor user behavior and detect abnormal activity. Varonis helps you prevent insider threats and data loss. You use automated alerts and detailed audit trails to investigate incidents. The platform supports data privacy tools and integrates with your existing security stack. Varonis scales for large enterprises and adapts to changing data volumes.
Website: https://www.varonis.com/data-security-platform
PKWARE Data Protection offers strong encryption and data masking capabilities. You use static data masking to protect information in databases. You perform safe analytics by masking data for authorized users only. PKWARE removes sensitive information from files and images with file and image redaction. You eliminate points of failure by ensuring no linkage between original and masked data. PKWARE uses pseudonymization and anonymization to de-identify personal information. You maintain consistent masking across various data stores. PKWARE SecureZIP provides enterprise-grade encryption with file-level protection. PK Encrypt secures data at rest, in use, or in motion for IBM Systems.
Website: https://www.pkware.com/
CipherTrust Data Security Platform supports multi-cloud environments and centralized key management. You secure data in public, private, and hybrid clouds. CipherTrust integrates with AWS, Azure, and Google Cloud. You manage encryption keys for BYOK, HYOK, and cloud-native encryption across clouds and on-premises systems. CipherTrust helps you protect sensitive data and meet privacy compliance requirements. You use it to automate compliance and enforce policies for data loss prevention.
Website: https://cpl.thalesgroup.com/encryption/data-security-platform
| Feature | Description |
|---|---|
| Securing data in the cloud | Solutions for protecting data in public, private, and hybrid cloud environments. |
| Integration with cloud platforms | Integrates with popular cloud platforms such as AWS, Azure, and GCP. |
| Centralized key management | Centralizes key management for BYOK, HYOK, and cloud-native encryption keys across various clouds and on-premises. |
IBM Guardium helps you discover, classify, and monitor sensitive data across databases and big data environments. You use Guardium to detect unauthorized access and prevent data loss. The platform supports automated compliance reporting for regulations like HIPAA and GDPR. You get real-time alerts and detailed audit logs. IBM Guardium integrates with your data security applications and supports large-scale deployments. You use it to protect enterprise data security and maintain business continuity.
Website: https://www.ibm.com/products/guardium
HashiCorp Vault manages secrets and encryption keys for your enterprise applications. You control the lifecycle of cryptographic keys, including creation, distribution, rotation, and revocation. Vault integrates with remote key management systems like Azure Key Vault and AWS KMS. You ensure secure transfer of key material and encryption at rest for cloud environments. Vault supports data protection in applications like Snowflake and enables compliance with privacy laws.
Website: https://www.hashicorp.com/en/products/vault
Egnyte Data Privacy Tools automate the discovery, classification, and monitoring of sensitive data across cloud and on-premises sources. You prevent unauthorized file access with sharing safeguards and granular permissions. Egnyte detects suspicious activities and alerts you to potential data loss. You use Egnyte to enforce privacy compliance and automate compliance workflows. The platform supports best data privacy software practices and helps you protect sensitive information.
Website: https://www.egnyte.com/solutions/data-security-and-governance
| Feature | Description |
|---|---|
| Sensitive Data Discovery and Classification | Automates the discovery, classification, and continuous monitoring of sensitive data across cloud and on-premises sources. |
| Data Leakage Protection | Prevents unauthorized file access with sharing safeguards and granular permissions, while detecting and alerting to suspicious activities. |
You need to compare data protection tools side by side to make the best choice for your business. The table below shows key features, pros, and cons for several top data security tools. You see how each tool handles data loss prevention, sensitive data, and privacy compliance.
| Tool Name | Key Features | Pros | Cons |
|---|---|---|---|
| Symantec Data Loss Prevention | Advanced data discovery, classification, cloud DLP | Highly scalable, strong compliance support | Complex setup, expensive for small businesses |
| Digital Guardian | Endpoint, network, cloud DLP, encryption, masking | Data-centric security, real-time insights | Steep learning curve, integration complexity |
| FineDataLink | Real-time synchronization, ETL/ELT, API integration | Visual interface, supports 100+ sources, cost-effective |
FineDataLink stands out with its real-time data synchronization and easy integration across more than 100 sources. You benefit from a user-friendly interface and flexible deployment.
You want data loss prevention that covers all types of sensitive data. Top data security tools use pattern matching, exact data matching, and document fingerprinting to find sensitive information. Machine learning and anomaly detection help you spot threats. Some tools use optical character recognition to scan images for sensitive text.
You get endpoint, network, and cloud DLP. Integrated DLP protects sensitive data in all environments. Content inspection and contextual analysis prevent unauthorized transfers. Policy enforcement and user behavior analytics help you stop insider threats. Data encryption and redaction keep sensitive data secure.
You need to know how much data protection software costs. Most solutions start at $10 per user per month. Full DLP suites cost about $52 per user per year. Endpoint-only modules are around $19 per user per year. Some vendors offer custom quotes with fair pricing. Falcon Enterprise charges about $184.99 per device per year. Premium tools require custom quotes and may have higher total costs.
| Deployment Model | Upfront Costs | Recurring Costs | Cost Efficiency |
|---|---|---|---|
| On-Premises | High | Low | Economical over time |
| Cloud | Low | Variable | Depends on usage |
| Hybrid | Moderate | Flexible | Combines both benefits |
You choose cloud, on-premises, or hybrid deployment. Hybrid solutions let you keep critical systems on-premises and use cloud resources for scalability. You optimize costs by matching workloads to the best platform.
Tip: FineDataLink gives you flexible deployment and affordable pricing. You automate compliance and build a strong data layer for analytics and privacy compliance.
You need to start by understanding your data loss prevention requirements. Look at the types of sensitive information your business handles. Use data classification to set protection levels for each type. Control access so only authorized staff can reach sensitive data. Train employees to spot threats and handle data securely. Build incident response plans to react quickly if a breach happens. Make sure your dlp solution works with your current data security systems. Stay compliant with regulations like gdpr compliance and ccpa compliance. Update and audit your dlp regularly to keep up with new threats.
| Factor | Description |
|---|---|
| Data Classification | Set protection levels for different data types. |
| Access Controls | Limit access to sensitive information. |
| Encryption | Protect data during transmission and storage. |
| Employee Training | Teach staff about threats and safe data handling. |
| Incident Response Plans | Prepare steps for breach or exposure. |
| Integration with Security Systems | Ensure dlp fits with existing data security applications. |
| Compliance with Regulations | Meet legal standards and avoid penalties. |
| Regular Updates and Audits | Keep dlp effective against new risks. |
You must choose data privacy software that fits your industry. Healthcare and finance need tools that support hipaa and privacy compliance. Intelation helps you protect electronic health records and meet strict rules. Spirion finds and secures sensitive data with high accuracy. IBM Consulting gives you risk analytics and compliance frameworks. PrivacyRef helps you build privacy programs and train staff. Use best data privacy software to manage sensitive data and meet privacy management software needs.
You need data protection tools that work with your current data security systems. Look for dlp solutions that connect with endpoint dlp, cloud platforms, and document security solutions. FineDataLink by FanRuan lets you integrate data from over 100 sources. You can synchronize sensitive data in real time and automate compliance workflows. Use APIs to share data between systems and reduce data exposure risk. Choose tools that support your business intelligence and enterprise data security goals.
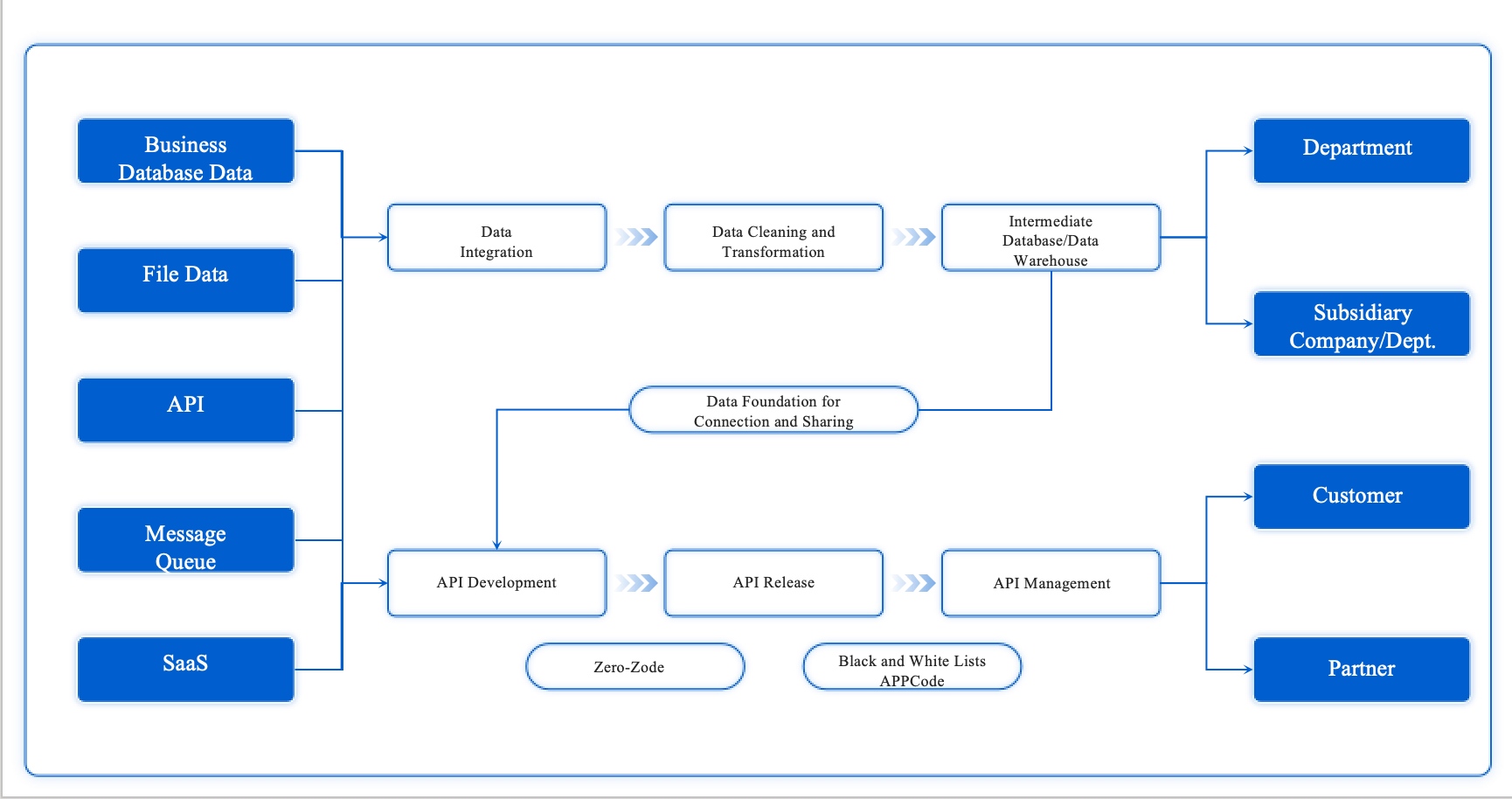
Tip: FineDataLink helps you build a strong data layer for analytics and privacy compliance. You get easy integration and real-time synchronization for sensitive information.
You must match your data protection strategy to your budget and growth plans. Small businesses need cost-effective dlp and data privacy software. Large enterprises require scalable solutions for complex data environments. Small businesses may spend up to 40% of their cybersecurity budget on managed services. Medium-sized businesses spend less, while large enterprises allocate more resources but still seek value. Choose top data security tools that scale with your needs and protect against insider threat protection and data exposure risk.
| Criteria | Small Enterprises | Large Enterprises |
|---|---|---|
| Scalability | Must grow with your business | Handles large volumes and complex needs |
| Cost-effectiveness | Focus on value and budget | More resources, but value still matters |
You need dlp, endpoint dlp, and data encryption to keep sensitive data safe as your business grows. Select data security tools that offer flexible pricing and deployment options. Use best data privacy software to support privacy compliance and document security solutions.
You want to see how top data protection tools stack up. The table below helps you compare their best features, pricing, and ideal use cases. You can use this overview to find the right fit for your business.
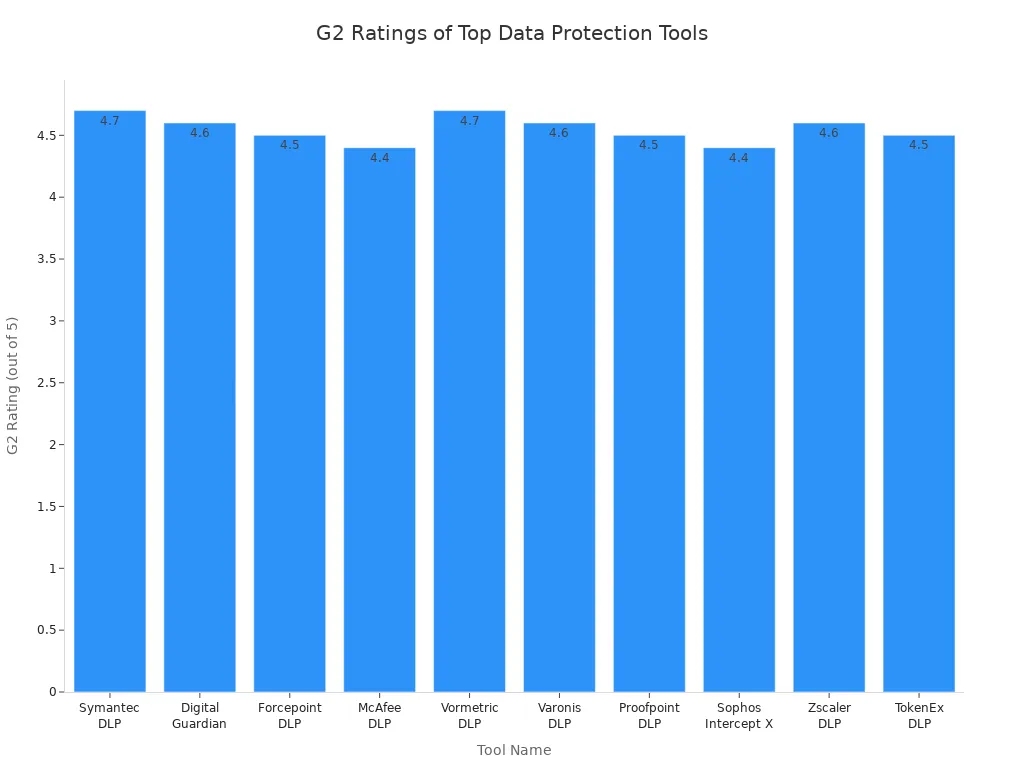
| Tool Name | Best For | Platform(s) Supported | Standout Feature | Pricing | Rating (G2) |
|---|---|---|---|---|---|
| Symantec DLP | Enterprises and SMBs | Windows, Mac, Linux | Full enterprise protection | Custom Pricing | 4.7/5 |
| Digital Guardian | Highly regulated industries | Windows, Mac, Linux | Comprehensive data protection | Custom Pricing | 4.6/5 |
| Forcepoint DLP | Enterprises | Web, Windows, Mac | Behavioral analytics | Custom Pricing | 4.5/5 |
| McAfee DLP | SMBs and large businesses | Windows, Mac, Mobile | All-in-one security suite | Starts at $59.99/year | 4.4/5 |
| Vormetric DLP | Enterprises | Web, Windows, Linux | Centralized policy management | Custom Pricing | 4.7/5 |
| Varonis DLP | Enterprises | Web, Windows, Mac | Insider threat detection | Custom Pricing | 4.6/5 |
| Proofpoint DLP | Cloud-first organizations | Web, Windows, Mac | Email-based DLP | Custom Pricing | 4.5/5 |
| Sophos Intercept X | SMBs with remote teams | Windows, Mac | Endpoint and cloud protection | Custom Pricing | 4.4/5 |
| Zscaler DLP | Cloud-native businesses | Web, Windows, Mac | Cloud-first DLP | Custom Pricing | 4.6/5 |
| TokenEx DLP | Financial and transactional data | Web, Windows | Tokenization | Custom Pricing | 4.5/5 |
| FineDataLink | Businesses with complex data integration needs | Web, Windows, Linux | Real-time data integration and synchronization | Affordable, flexible | N/A |
FineDataLink by FanRuan stands out for its ability to connect and harmonize data from many sources. You solve problems with data silos and keep your business intelligence reliable. This tool works well for companies that need to integrate data from different systems and want a user-friendly platform.
Tip: If you manage data from multiple sources, FineDataLink helps you build a strong data foundation for analytics and compliance. You get real-time synchronization and easy integration, which saves time and reduces errors.
You can use this table to match your business needs with the right data protection tool. Each solution offers unique strengths, so you should choose the one that fits your workflow, budget, and security goals.
You need strong data protection tools to keep your business safe in 2025. DLP and data privacy software help you protect sensitive information and meet legal standards.
Tip: Start a free trial or talk with a data security expert to find the best fit for your business.

The Author
Howard
Data Management Engineer & Data Research Expert at FanRuan