Data exposure occurs when sensitive information becomes accessible to unauthorized individuals, often unintentionally. This issue has grown critical in the digital age. For instance, in 2023, over 353 million individuals were affected by 3,205 data compromises, a staggering 78% increase from 2022. Unlike a data breach, which involves malicious intent, data exposure often stems from negligence or misconfigurations. The financial impact is immense, with the average cost of a data breach in the US reaching $4.88 million. Protecting corporate data is no longer optional—it is essential for safeguarding trust and resources.
Key Takeaways
- Data Exposure Risks: Mistakes in security settings and human errors often cause data leaks, harming millions and leading to identity theft or financial loss.
- Prevention Measures: Regular checks, employee training, strong passwords, and two-factor authentication are essential to protect data.
- Tools and Trust: Solutions like FineDataLink and FineBI enhance data safety, build trust, and ensure compliance with regulations.
Understanding Data Exposure

What is Data Exposure?
Data exposure happens when sensitive information becomes accessible to unauthorized individuals, often unintentionally. This can occur due to misconfigured systems, human mistakes, or weak security measures. Unlike a deliberate attack, data exposure typically results from oversight or negligence. For example, leaving a database without proper password protection can lead to sensitive data being visible to anyone online.
The consequences of data exposure can be severe. Sensitive information, such as personal details, financial records, or intellectual property, may fall into the wrong hands. This can lead to identity theft, financial loss, or reputational damage. In 2023, over 353 million individuals were impacted by 3,205 reported data compromises. These numbers highlight the growing importance of addressing data exposure in today’s digital world.
| Year | Average Cost of Data Breach | Reported Data Compromises | Individuals Impacted | | --- | --- | --- | --- | | 2020 | $3.86 million | N/A | N/A | | 2023 | N/A | 3,205 | 353,027,892 |
How Data Exposure Differs from Data Breaches
You might wonder how data exposure differs from a data breach. While both involve unauthorized access to sensitive information, the key difference lies in intent. Data exposure often occurs accidentally. For instance, a company might misconfigure its cloud storage, leaving files publicly accessible. On the other hand, a data breach involves malicious intent, such as hackers infiltrating a system to steal data.
Understanding this distinction is crucial. Data exposure can happen even if no one actively tries to exploit your systems. It underscores the need for proactive measures, such as regular security audits and proper configuration of digital assets. By addressing vulnerabilities early, you can reduce the risk of both exposure and breaches.
Real-World Examples of Data Exposure
Real-world cases illustrate the impact of data exposure. Here are some notable examples:
- The global average cost of a data breach reached $3.86 million in 2020.
- Breaches often remain undetected for an average of 280 days, giving attackers ample time to exploit exposed data.
- Sensitive data exposure can harm an organization’s reputation and financial stability.
In the United States, the average cost of a data breach is $9.44 million. Additionally, 9.6% of companies worldwide are expected to experience at least one data breach in the next two years. Cybercrime, including data exposure incidents, could cost the global economy up to $10.5 trillion by 2025. These figures emphasize the urgency of safeguarding sensitive information.
Tip: Regularly review your organization’s security settings and train employees on best practices to minimize the risk of data exposure.
Causes of Sensitive Data Exposure
Sensitive data exposure often results from unintended instances where vulnerabilities in systems or human actions compromise sensitive personal data. Understanding the causes of sensitive data exposure is essential for mitigating risks and protecting information.
Common Causes of Sensitive Data Exposure
Misconfigured Security Settings
Misconfigured security settings are among the leading causes of sensitive data exposure. For example, leaving cloud storage buckets publicly accessible can expose sensitive personal data to unauthorized users. Misconfigurations often occur due to oversight during system setup or updates. According to recent statistics, misconfiguration accounts for 21% of incidents involving sensitive data exposure. Organizations must regularly audit their systems to identify and correct these vulnerabilities.
Human Error and Negligence
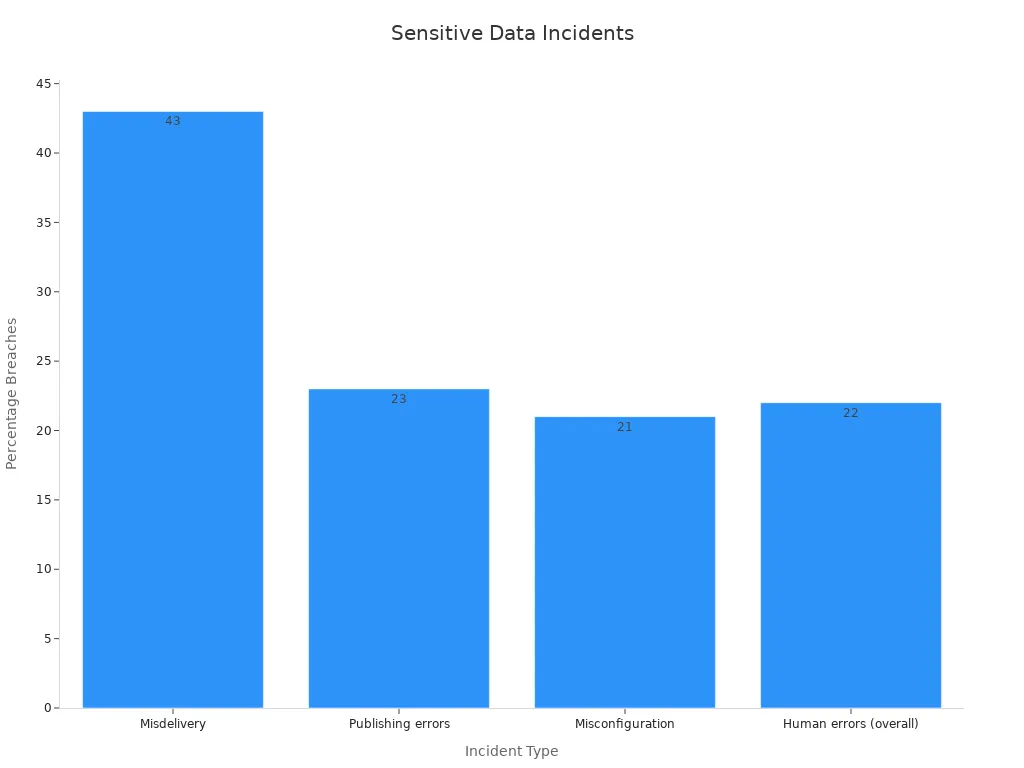
Human error plays a significant role in accidental data exposure. Employees may inadvertently send sensitive personal data to the wrong recipients or fail to follow security protocols. Misdelivery alone accounts for 43% of such incidents. Negligence, such as using weak passwords or failing to encrypt sensitive files, further exacerbates the problem. Training employees on data security practices can significantly reduce these risks.
Insider Threats
Insider threats, whether intentional or accidental, pose a unique challenge. Malicious insiders may exploit their access to sensitive personal data for financial gain, while unintentional actions, such as sharing information without proper authorization, can lead to exposure. Insider-led cyber incidents cost organizations an average of $16.2 million annually. Implementing robust access controls and monitoring employee activity can help mitigate these threats.
| Type of Incident | Percentage of Breaches | | --- | --- | | Misdelivery | 43% | | Publishing errors | 23% | | Misconfiguration | 21% | | Human errors (overall) | 22% |
Mechanisms of Accidental Data Exposure
Unsecured Networks and Devices
Unsecured networks and devices are common avenues for accidental data exposure. Public Wi-Fi networks, for instance, lack encryption, making sensitive personal data vulnerable to interception. Similarly, lost or stolen devices without proper security measures can lead to unintended instances of exposure. Always use secure networks and enable device encryption to safeguard sensitive information.
Vulnerabilities in Software or Systems
Software vulnerabilities, such as outdated applications or unpatched systems, create openings for attackers to exploit. SQL injection attacks, where malicious users manipulate server requests, are a prime example. Weak encryption protocols also contribute to accidental data exposure, leaving sensitive personal data unprotected during transactions. Regular updates and vulnerability assessments are crucial for maintaining system security.
Accidental Sharing of Sensitive Information
Accidental sharing occurs when sensitive personal data is disclosed to unauthorized individuals. This can happen through phishing attacks, where users unknowingly provide information to malicious actors, or through publishing errors, which account for 23% of exposure incidents. Educating employees about phishing tactics and implementing review processes for public-facing content can minimize these risks.
Note: Protecting sensitive personal data requires a proactive approach. Regular audits, employee training, and robust security measures can significantly reduce the causes of sensitive data exposure.
Consequences of Data Exposure
Data exposure can have far-reaching consequences, affecting both individuals and organizations. Understanding these impacts helps you recognize the importance of safeguarding sensitive information.
Impacts on Individuals
Identity Theft and Financial Loss
When personally identifiable information becomes exposed, identity theft often follows. Cybercriminals can use your personal information to open fraudulent accounts, apply for loans, or make unauthorized purchases. These actions can lead to significant financial losses and damage your credit score. For example, exposed credit card details or Social Security numbers can result in unauthorized transactions, leaving you to deal with the aftermath. Recovering from identity theft is time-consuming and stressful, often requiring legal assistance and extensive documentation.
Loss of Privacy
Sensitive data exposure compromises your privacy. Personal details, such as medical records or home addresses, may become accessible to unauthorized individuals. This loss of privacy can lead to emotional distress and even physical risks. For instance, exposed medical records might reveal confidential health conditions, causing embarrassment or discrimination. Protecting your privacy requires vigilance, such as limiting the sharing of personal information and using secure platforms.
Impacts on Organizations
Reputational Damage
For organizations, data exposure can severely harm their reputation. Customers trust businesses to protect their personally identifiable information. When a data breach or exposure occurs, that trust erodes. Negative publicity spreads quickly, especially in the digital age, leading to a loss of credibility. Companies often struggle to regain public confidence after such incidents. A tarnished reputation can result in decreased customer loyalty and reduced market share.
Financial Penalties and Legal Consequences
Organizations face significant financial penalties for failing to protect sensitive data. Regulatory bodies have increased enforcement of data protection laws, with fines exceeding $1 million becoming more common. Legal consequences also include lawsuits from affected individuals or entities. These penalties and legal actions strain resources and disrupt operations. Ensuring compliance with data protection regulations is essential to avoid these costly outcomes.
Loss of Customer Trust
Data exposure directly impacts customer trust. When customers learn their personal information has been compromised, they may hesitate to continue doing business with the organization. This loss of trust affects customer retention and acquisition. Building trust takes years, but a single incident of sensitive data exposure can undo that effort. Transparent communication and robust security measures are critical for maintaining customer confidence.
Note: The impact of sensitive data exposure extends beyond immediate financial losses. It affects relationships, trust, and long-term growth. Proactively addressing vulnerabilities can help you mitigate these risks effectively.
How to Prevent Data Exposure
Best Practices for Preventing Sensitive Data Exposure
Use Strong Passwords and Enable Two-Factor Authentication
Strong passwords act as the first line of defense against data security threats. Use unique combinations of letters, numbers, and symbols to make passwords harder to guess. Avoid reusing passwords across multiple accounts. To further enhance security, enable two-factor authentication (2FA). This adds an extra layer of protection by requiring a second verification step, such as a code sent to your phone. Using salted hashing functions for password storage also prevents unauthorized access. These measures significantly reduce the risk of sensitive data exposure.
Regularly Audit and Update Security Configurations
Conducting regular audits helps identify vulnerabilities in your systems. Misconfigured security settings often lead to data exposure. Review access controls and ensure only authorized personnel can access sensitive information. Disable autocomplete and caching features to prevent cached data vulnerabilities. Regular updates to software and systems also address potential weaknesses. By staying proactive, you can minimize risks and strengthen your data protection measures.
Train Employees on Data Security Protocols
Employees play a crucial role in preventing data exposure. Provide training on recognizing phishing attempts and handling sensitive information securely. Teach them to classify data and follow the principle of least privilege when sharing access. Awareness of data security threats empowers employees to act responsibly. Regular training sessions ensure everyone stays updated on best practices, reducing the likelihood of accidental exposure.
Tip: Identify and encrypt sensitive data both at rest and in transit to add an extra layer of security.
Advanced Solutions for Preventing Data Exposure
Leveraging FineDataLink for Real-Time Data Synchronization
FineDataLink offers a robust solution for managing data integration and data synchronization. Its real-time data synchronization capabilities ensure that sensitive data remains secure during transfers. By consolidating data from multiple sources, FineDataLink reduces the risk of data silos and enhances data governance. Its low-code platform simplifies complex processes, making it easier to implement stringent access controls. This tool helps organizations prevent sensitive data exposure while maintaining operational efficiency.
Using FineBI for Data Governance and Access Control
FineBI empowers organizations to manage data governance effectively. It provides role-based access controls, ensuring that only authorized users can access sensitive information. FineBI also supports data classification, helping you identify and secure critical data. Its self-service analytics feature allows users to explore data without compromising security. By integrating FineBI into your workflow, you can strengthen your data protection measures and reduce exposure risks.
Employing FineReport for Secure Data Visualization
FineReport combines advanced data visualization with robust security features. Its zero-code interface allows users to create dashboards without exposing sensitive data. FineReport supports real-time analytics, enabling you to monitor data security threats as they arise. The platform’s adaptive design ensures secure access across devices, enhancing flexibility without compromising safety. FineReport provides a comprehensive solution for visualizing data securely, making it an essential tool for modern organizations.
Note: Advanced solutions like FineDataLink, FineBI, and FineReport not only enhance security but also improve efficiency and decision-making.
Why Proactive Measures Against Data Exposure Are Essential
The Cost of Reactive Approaches to Data Exposure
Reacting to data exposure after it occurs can lead to significant financial and operational setbacks. When sensitive data exposure happens, organizations often face immediate consequences like reputational damage, operational disruptions, and regulatory penalties. These issues not only drain resources but also hinder long-term growth.
| Consequence | Description | | --- | --- | | Loss of reputation | Data breaches can damage an organization's integrity, leading to a loss of customer trust and revenue. | | Operational outage | Addressing data exposure vulnerabilities can halt daily operations, significantly affecting finances. | | Compliance penalties | Organizations may incur fines from regulatory bodies for failing to protect sensitive data. |
For example, operational outages caused by addressing vulnerabilities can disrupt daily activities, leading to financial losses. Similarly, compliance penalties for failing to protect sensitive data can cost millions. These reactive measures often cost more than implementing proactive strategies. By addressing vulnerabilities early, you can avoid these costly consequences and maintain business continuity.
Note: Proactive measures save you from the high cost of sensitive data exposure. They protect your reputation, ensure compliance, and prevent operational disruptions.
Benefits of Proactive Data Protection
Enhanced Security and Compliance
Proactive data protection strengthens your security framework. Regular audits, encryption, and access controls reduce the risk of data exposure. These measures also help you comply with data protection regulations, avoiding hefty fines. For instance, organizations that prioritize security often experience fewer breaches, saving millions in potential recovery costs. Enhanced compliance not only protects your finances but also builds a culture of accountability within your organization.
Building Trust with Customers and Stakeholders
Proactive data protection fosters trust. Customers feel confident sharing their information when they know it is secure. This trust translates into loyalty and long-term relationships. Additionally, stakeholders view organizations with strong data protection measures as reliable and forward-thinking.
| Benefit | Description | | --- | --- | | Cost Reduction | Proactive measures can significantly lower the costs associated with data breaches and recovery. | | Reputation Enhancement | Organizations that prioritize data protection are viewed more favorably by customers and partners. | | Competitive Advantage | Companies with strong data protection can differentiate themselves in the market. | | Improved Efficiency | Streamlined security processes lead to better operational efficiency. | | Increased Agility | Organizations can respond more quickly to threats and changes in the security landscape. |
Proactive strategies also give you a competitive edge. Companies with robust data protection stand out in the market. They attract more customers and partners, enhancing their reputation and profitability. By investing in proactive measures, you not only protect sensitive data but also position your organization for long-term success.
Tip: Building trust through proactive data protection strengthens your brand and ensures customer loyalty.
Key Takeaways on Data Exposure
Recap of What Data Exposure Is
Data exposure occurs when sensitive information becomes accessible to unauthorized individuals due to failed security measures. Unlike deliberate breaches, it often results from unintentional actions like misconfigured systems or human error. Sensitive data exposure can lead to severe consequences, including identity theft, financial loss, and reputational damage.
Key characteristics of data exposure include:
- It typically happens unintentionally, often due to negligence or weak security protocols.
- Common causes include misconfigured systems, insider threats, and software vulnerabilities.
- Proactive measures like encryption, access restrictions, and regular audits can mitigate risks.
| Characteristic/Measure | Description | | --- | --- | | Definition | Sensitive data exposure occurs when security measures fail to protect sensitive information from unauthorized disclosure. | | Causes | Misconfigured systems, human error, inadequate security measures. | | Nature | Typically unintentional and can lead to unauthorized access to sensitive data. | | Proactive Measures | Implementation of encryption, data masking, and access restrictions. | | Responsive Strategies | Security audits, incident response systems, and prompt reaction to breaches. |
Understanding these aspects helps you recognize the importance of safeguarding sensitive information.
Summary of Prevention Strategies
Preventing data exposure requires a combination of best practices and advanced tools. Organizations that adopt proactive strategies significantly reduce risks and costs associated with sensitive data exposure.
Here are some effective prevention strategies:
- Implement Security Automation: Saves an average of $1.76 million per breach.
- Develop Incident Response Plans: Reduces costs by $2.66 million and improves response times.
- Encrypt Data: Protects sensitive information and saves $220,000 on average.
- Leverage AI and Automation: Enhances detection and saves $1.88 million.
- Faster Detection and Response: Cuts response time by nearly 100 days, minimizing damage.
| Prevention Strategy | Average Cost Savings | | --- | --- | | Implementing security automation | $1.76 million | | Developing incident response plans | $2.66 million | | Encrypting data | $220,000 | | Leveraging AI and Automation | $1.88 million | | Faster detection and response | Nearly 100 days faster |
Training employees, conducting regular audits, and using tools like FineDataLink, FineBI, and FineReport further strengthen your defenses. These tools provide real-time synchronization, secure data governance, and advanced visualization, ensuring sensitive data remains protected.
Final Thoughts on the Importance of Proactive Data Protection
Proactive data protection is essential in today’s cybersecurity landscape. It allows you to anticipate and block threats before they occur, reducing the likelihood of sensitive data exposure. Regular security assessments and employee training help identify vulnerabilities and mitigate risks associated with human error.
Adopting a proactive approach offers several benefits:
- Strengthens defenses against evolving threats.
- Builds trust with customers and stakeholders.
- Reduces financial losses and operational disruptions.
- Enhances compliance with privacy laws and regulations.
Tip: Continuous monitoring and vulnerability assessments are critical for staying ahead of potential risks. By investing in proactive measures, you not only protect sensitive data but also position your organization for long-term success.
Proactive data protection is not just a strategy—it is a necessity. It safeguards your organization’s future while fostering trust and resilience in an increasingly digital world.
Data exposure occurs when sensitive information becomes accessible to unauthorized individuals due to weak security measures or human error. This issue can lead to severe consequences, including reputational damage, operational disruptions, and compliance penalties.
| Consequence | Description | | --- | --- | | Loss of reputation | Organizations face a loss of integrity, leading to decreased customer trust and potential revenue loss. | | Operational outage | Costs associated with detecting and remediating vulnerabilities can halt day-to-day operations. | | Compliance penalties | Organizations may incur fines from regulatory bodies for failing to protect sensitive data. |
Understanding the causes, such as misconfigured systems or insider threats, helps you address vulnerabilities effectively. Proactive measures, like regular audits and advanced tools, reduce risks and save costs. For instance, the average cost of data recovery reaches $1.1 million per incident, with $204 spent per employee. By acting now, you protect sensitive information and build trust for the future.
| Metric | Value | | --- | --- | | Average cost of data recovery | $1.1 million per incident | | Average cost per employee | $204 |
Tip: Safeguarding data today ensures a secure and resilient tomorrow.
FAQ
Data exposure happens unintentionally, often due to misconfigurations or human error. A data breach involves malicious intent, like hacking or theft. Both compromise sensitive information, but exposure typically results from negligence, while breaches are deliberate attacks.
Look for unusual activity, such as unauthorized transactions or login attempts. Notifications from companies about security incidents may also indicate exposure. Regularly monitor your accounts and use identity theft protection services to stay informed.
The digital age has increased the amount of sensitive information stored online. Misconfigured systems, human errors, and insider threats make data exposure more common. The financial and reputational consequences for individuals and organizations highlight the need for stronger security measures.
Use strong passwords, enable two-factor authentication, and encrypt sensitive data. Regularly audit your security settings and train employees on best practices. Advanced tools like FineDataLink, FineBI, and FineReport can also enhance your data protection efforts.
FineDataLink ensures real-time data synchronization and secure integration across systems. Its low-code platform simplifies complex processes, reducing the risk of misconfigurations. By consolidating data and enhancing governance, it minimizes vulnerabilities that lead to exposure.
Act quickly. Change your passwords and enable two-factor authentication. Notify affected parties and monitor your accounts for suspicious activity. Consider freezing your credit to prevent identity theft. Seek professional assistance if necessary.
Employees often handle sensitive information. Without proper training, they may fall victim to phishing scams or make errors that lead to exposure. Educating your team on security protocols reduces risks and strengthens your organization’s defenses.
Yes, many tools like FineDataLink and FineBI offer scalable solutions suitable for small businesses. These tools provide cost-effective ways to secure data, streamline operations, and comply with regulations, making them accessible even for smaller budgets.
Continue Reading About Data Exposure
2025 Best Data Integration Solutions and Selection Guide
Explore top data integration solutions for 2025, enhancing data management and operational efficiency with leading platforms like Fivetran and Talend.
Howard
Dec 19, 2024
10 Game-Changing Project Management Reporting Types!
Unlock project success with 10 must-know reporting types! Track progress, manage risks, and stay on budget like a pro.
Lewis
Mar 03, 2025
2025's Best Data Validation Tools: Top 7 Picks
Explore the top 7 data validation tools of 2025, featuring key features, benefits, user experiences, and pricing to ensure accurate and reliable data.
Howard
Aug 09, 2024